Introduction
Since March 2018, violent demonstrations have been taking place on the Gaza-Israeli border. The so-called ‘Great March of Return’ has been gathering thousands of Palestinians every Friday, leading to riots, attempts to break through the border fence and clashes with the Israeli military forces. Starting from May, Hamas and Palestinian Islamic Jihad launched a series of rocket and mortar attacks on Israeli territory, followed by the Israeli Air Force’s retaliation strikes and reinforcement of the blockade of the Gaza Strip, which resulted in deterioration of the humanitarian situation in the enclave. Simultaneously, terrorist organisations operating from the Gaza Strip began arson attacks, using kites and helium balloons with flammable materials and IEDs attached, which had been flown to the Israeli side of the border, causing wide-scale fires and destruction of civilian property. The latest round of hostilities in the Israeli-Palestinian conflict can serve as an example of the adaptation of tactics used by Hamas and other Palestinian armed groups to the changing reality of the conflict. This method of massive arson attacks provided the Palestinians an occasion to by-pass the advanced Israeli defence system, which appeared to be unprepared for this relatively simple, yet uncontrollable threat.
The aim of this article is to analyse the use of weaponised incendiary kites and helium balloons in the Israeli-Palestinian border hostilities. The paper argues that arson started with incendiary kites and balloons can be easily exploited for terrorist purposes and poses a serious challenge to regular armed forces as well as civilian emergency services. The study focuses on the arson attacks that took place in the Western Negev region in Israel between March and December 2018. The author is seeking answers to two main questions: why are the kites and balloons useful for the current goals of Hamas and how do the Israeli army, security services and policy-makers respond to this new threat? The overall findings of this paper present the threat of arson terrorism in the context of an asymmetric warfare.
Background: Palestinian ‘Great March of Return’
Major clashes along the Gaza-Israeli border began on 30 March 2018, yet the reasons for the most recent escalation reach back to December 2017 and the decision of the U.S. President Donald Trump to move the American embassy and to recognise Jerusalem as the capital of Israel. As a response to this decision, protests were held both in the West Bank and in the Gaza Strip. As soon as the date of the embassy relocation was announced, rumours about the ‘Great March of Return’ appeared in the media. The march, initially planned by the civil activists from the Gaza Strip, was soon taken over by Hamas members who became a driving force behind the most violent events at the border, even though the majority of participants were in fact civilians (Michael 2018). The largest demonstration was supposed to take place on 14 May, to show the opposition of the Palestinians to the decision of the U.S President and to demand an easing of the blockade imposed on the Gaza Strip by Israel and Egypt in 2007. Demonstration camps were set up along the border and the first large protest, initially non-violent, took place on 30 March 2018, gathering between 30,000 and 40,000 Palestinians (Al-Omari and Herzog 2018, p. 2). Even though most of participants refrained from violence, groups of protesters began burning tyres, throwing stones, Molotov cocktails and grenades and attempted to break through the border barrier, to which the Israeli military responded with gunfire and tear gas. The situation escalated into riots, which continued – on a smaller scale – every Friday until 14 May: the day of the U.S. embassy relocation and the day when (according to the Georgian calendar) Israel marked its 70th anniversary of independence1. According to Brand, Shuker and Slman-Tov (2018), the protests on this day peaked to over 40,000 participants again and the riots were the most violent and the most deadly, with 60 Palestinian fatalities and thousands of injured. Clashes and demonstrations in the border area continued every Friday until the end of 2018 and still take place in 2019 with varied turnouts.
At the end of May 2018, Hamas and Palestinian Islamic Jihad renewed rocket and mortar barrage, directed at the Israeli neighbourhoods located near the Gaza border. According to the Israeli Security Agency reports (2018), the biggest number of attacks was noted in July (67 attacks), August (83 attacks) and in November, when after one relatively calm month the rockets were launched again, causing a retaliation airstrike by the Israeli Air Forces, during which approximately 80 targets in the Gaza Strip were destroyed, including weapon storages, rocket launchers and Hamas’ offices. At the end of October, the Israel Defence Forces (further: IDF) reinforced positions in the border area with tanks, artillery, combat engineers and infantry troops. The most violent escalation of the hostilities took place between 11 and 13 November 2018, when Hamas fired over 400 rockets and mortars as a response to foiled Israeli special forces mission in the Gaza Strip. The IDF responded with intensive airstrikes. After he UN and Egypt brokered a ceasefire, the situation at the border noticeably calmed down, despite the rumours of a full-scale war. The Friday protests have been continued, but in a less violent form and the number of participants has decreased.
The ‘Great March of Return’ failed to achieve most of its goals: the U.S. embassy was successfully moved to Jerusalem and the blockade of the Gaza Strip not only remained in force, but the restrictions were tightened as a response to Hamas’ attacks (UN Office for the Coordination of Humanitarian Affairs 2018). The protesters did not manage to break through the border fence. Most rockets and mortars launched from the enclave, even though they kept forcing the Israelis living in the Gaza periphery to run to shelters, either fell in the desert and fields or were successfully intercepted by the Iron Dome air defence system, causing no casualties. The relocation of the U.S. embassy gained more media attention than the mass protests along the border and the weekly gatherings have gradually attracted fewer Palestinian civilians, who became dissatisfied with the lack of noticeable achievements, the high numbers of fatalities and injured protesters. Frustration caused by the lack of military and political success pushed the Hamas command to come up with a new modus operandi that would allow at least partial victory to be claimed and the difficulties of prolonged hostilities to be justified to the people. The concept of airborne incendiary devices turned out to be an effective solution. Images of large arson attacks became powerful tools, used by Hamas to boost morale of the Gazans and to keep their political support. Simultaneously, the attacks damaged the Israeli economy and, most of all, had a significant psychological impact on the residents of the Western Negev region.
How did the kites and balloons become weapons?
The use of kites and balloons for combat purposes is not an original invention of Hamas. It is believed that the kites were already being used by the Chinese armies in the 2nd century B.C. According to the chronicle written in 1326 by Walter de Milemette, they were also used in medieval Europe to drop firebombs over the walls of besieged cities (Murphy 2005, p. 2). The idea of balloon-bombs dates back to the 18th century, when the fist combat use of hot air balloons carrying bombs took place at the siege of Venice during the Italian War of Independence (1848-1849). In the 1930s and 1940s the concept was further developed in Japan. Between 1944 and 1945, over 9,000 large intercontinental balloons carrying incendiaries and anti-personnel bombs (so-called Fu-Go weapons) were launched from Japan to reach American territory (Mikesh 1973, pp. 1–5). Hydrogen balloons were commonly used by the British army during Operation Outward in 1942-1944 as well. Equipped either with trailing wires or incendiary devices, they were used to damage high-voltage power lines or to start massive fires in Germany and occupied Europe (Drapeau 2011, pp. 94–101). In the 1950s, the U.S. military tested hydrogen-filled balloons (known as E77 balloon bomb and WS124A Flying Cloud) that could deliver biological and chemical weapons to targets in the Soviet Union, but they never went operational because of their poor accuracy (Whitby 2002, pp. 164–166). Due to rapid evolution of modern warfare, weaponised balloons ceased to have significance for regular armies and until the second decade of the 21st century, their only military utility was for reconnaissance purposes.
The first kites bearing flammable items were spotted in southern Israel on 13 April 2018, two weeks after the first demonstration along the border fence. They were constructed from easily available materials: sticks, paper, light fabric or plastic wrap, with burning objects attached to long strings. Some kites displayed in the Palestinian media or found inside the Israeli territory were decorated with Palestinian flags, pictures of people considered martyrs or with slogans related to the ideas of the ‘Great March of Return’. Being able to ignite fires only in the nearest Israeli farms, they were soon replaced with light helium balloons that could fly higher, reach deeper into the Israeli territory and thus did not necessarily have to be launched close to the guarded border fence. Just as for the kites, small pouches containing oil-soaked materials or pieces of coal were attached to the balloon strings and set on fire before launching (Gross 2018a). Balloons carrying improvised explosive devices (IEDs) were found inside the Israeli territory in June 2018, many of them being colorful party balloons with cartoon decorations, apparently aimed at attracting children. It is not clear who initially came up with the idea of flying burning objects and IEDs above the border fence, but the first media reports of the IDF identified the Palestinian youth taking part in the weekly demonstrations. As soon as the arson attacks proved to work, Hamas command got involved and began to co-ordinate multiple attacks carried out both by the militants and by the sympathisers of the organizsation. The Hamas-affiliated ‘al-Zouari unit’2 was created and presented as a cell which specialises in construction and launching fire kites and balloons. The Hamas leadership officially declared protection over anyone participating in the arson attacks. They also claimed a propaganda success after the fires sparked outrage in Israel (Meir Amit Intelligence and Terrorism Information Center 2018, pp. 3–5).
Arson attacks gathered momentum between July and September 2018, with an average of 12 fires a day. The number of reported fires decreased with the end of the dry summer season. This general tendency was confirmed by various media reports, IDF and government statements; however, complete statistics showing the exact number of attacks per each month between March and December have not been published yet3. Depending on the wind, most of the kites and balloons fell within a few kilometres from the border fence, although there were balloon clusters bearing IEDs that managed to reach Be’er Sheva city, located approximately 40 kilometres from the Gaza Strip. The vast majority of large-scale fires occurred in the so-called ‘Gaza Envelope’, which includes the city of Sderot and agricultural areas surrounding the Gaza Strip from the East and North. The fresh tactic allowed Hamas to challenge the Israeli military and emergency services. The defence system of the southern border, extensively developed over the last few years in order to combat rocket and mortar fire, was initially incapable of dealing properly with this unprecedented threat. Fields and nature reserves in the areas in the ‘Gaza Envelope’ suffered severe losses. According to the data released to the press by the Israeli Nature and Parks Authority in December 2018, approximately 8,000 acres (over 32 square kilometers) of land went up in flames due to incendiary kites and balloons, two thirds of that being nature reserves and the remaining part consisting of farmlands, mainly wheat fields (Rinat 2018). Several farm buildings and pastures burned down, killing farm animals; there were also reports of beehives destroyed by the fire. Israeli authorities proclaimed the fires an ecological disaster as many wild species lost their natural habitat and full recovery of natural reserves could take years in the dry area of the Western Negev. According to the Israeli Tax Authority, losses of local farmers that would be compensated by the government reached over 3 million USD (Rinat 2018).
Incendiary balloons and kites were most effective as a psychological weapon. Not only did they manage to evoke fear and a feeling of helplessness among the residents of the ‘Gaza Envelope’, but also resulted in protests by the affected Israeli citizens against their own government. Claiming that the decision-makers were not doing enough to end the tense situation at the border, they blocked the roads in major cities in the South, burned tyres and organised a 90-kilometre march from Sderot to Jerusalem to protest in front of the Knesset (Siman-Tov and Schweitzer 2018, p. 3).
The use of weaponised kites and balloons for terrorist purposes
The Israeli-Palestinian conflict is often cited in certain research as a typical example of an asymmetric conflict (e.g. Cohen and White 2009, Gallo 2009, Kardelj 2010, Siman-Tov 2007). Thus, the purpose of Hamas and other armed organisations from the Gaza Strip is to undermine Israeli military supremacy with tactics which are difficult to combat for regular armed forces and which require disproportionate effort from the Israeli side. The last decade of the Israeli-Palestinian conflict has been dominated by two major tactics, commonly used by Hamas: short-range rocket fire and underground cross-border tunnels enabling infiltration of Israeli territory. Since the IDF came up with effective technological and tactical countermeasures to those challenges and, additionally, the ‘Great March of Return’ did not go as planned, Hamas needed a new tactic that would allow the organisation to claim easy victory and boast the morale of its supporters. The phenomenon of incendiary kites and balloons provided an ideal temporary solution to the lack of visible success with rocket attacks or infiltration. The arson attacks can also serve as a good example of asymmetric warfare, which benefits the weaker side of the conflict. The following list indicates some of the benefits of weaponised kites and balloons for terrorist purposes, which have been exploited by Hamas since April 2018:
The materials used to produce incendiary kites and balloons are much cheaper, compared to the cost of manufacturing rockets or materials and equipment required to dig and secure underground tunnels. The cost of Qassam rockets (most commonly used by Hamas) can reach up to 800 USD per each. According to Watkins and James (2016, p. 95), the construction and maintenance of one cross-border tunnel is estimated to cost approximately 1 million USD, while the IDF authorities estimated the cost to vary between 3 and 10 million USD, depending on the length and depth of the tunnel (COGAT 2017). For comparison, the cost of materials used to build an incendiary kite or a balloon does not exceed a few dollars. Therefore, Hamas and their supporters have managed to acquire large amounts of incendiary kites and balloons without damage to their budget;
Materials used to construct incendiary kites and balloons are easily available in the Gaza Strip, unlike those needed to build the tunnels or manufacture rockets and handguns. Most concrete pipes, cement and iron, used by Hamas to secure the tunnels, come from confiscation of the building materials transferred regularly to the Gaza Strip as humanitarian assistance. Due to the supervision of the UN authorities, strict Israeli border control and lack of domestic industry, access to those materials remains limited. The rockets and mortars used by Hamas are either smuggled in through the underground tunnels from the Egyptian Sinai or built in the Gaza Strip from parts coming from the same source. The Egyptian army, however, actively participates in the joint effort to combat the tunnels together with the IDF, so Hamas’ opportunities to acquire weapons depend on the current security situation in the Sinai. For example, between 2011 and 2015, the Egyptian army destroyed almost 2,000 smuggling tunnels and, since 2015, Egypt has started deploy more digging sensors and to widen the no-go ‘buffer zone’ in the Sinai, which makes it more difficult for Hamas members to reach the areas where any purchase and transport of weapons could occur (Shay 2016, pp. 1–2). In this situation, incendiary kites and balloons made of cheap, everyday-use materials, provided Hamas with a convenient substitute of other hardly available weapons. Even though most supplies from abroad come to the Gaza Strip through the IDF-controlled land crossings, products like party balloons, paper, fabric or plastic wrap have not been limited in any way, neither has coal or flammable liquids. In June 2018, when the Israeli Ministry of Defence confirmed the information that Hamas had acquired helium to fill the arson balloons from the deliveries to the hospitals4, the entry of this gas to the Gaza Strip was limited (Gross 2018b). Despite more rigorous assessment of the requests made by the Palestinian hospitals, Hamas still managed to obtain enough helium to continue the offensive;
The fact that the new weapon is relatively cheap and easy to build, made it possible for non-member supporters of Hamas to participate in the attacks with no need to rely on central funding. There is also no need for trained personnel to launch the incendiary kites and balloons, as in the case of rockets or mortars. Thus, this tactic allows Hamas to coordinate multiple attacks at the same time without employing all of its members for one task. Participation of civilian supporters in the attacks also helps Hamas to build the narrative of ‘popular resistance’ for propaganda purposes (Al-Omari and Herzog 2018, p. 3);
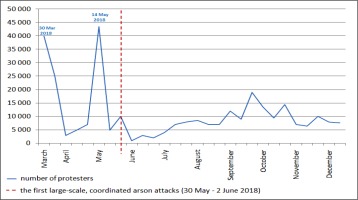
Along with the arson attacks, the media associated with Hamas launched an information campaign targeted mainly at the Palestinian public. Images of large fires, burned Israeli fields and destroyed property have been published as evidence of Hamas’ military capbilities. They were also used to claim victory over Israeli technological supremacy, which turned out to be insufficient in the face of arson attacks. Propaganda efforts have been focused on presenting the limited military response of the IDF as a sign of helplessness and avoidance of escalation as a proof of weakness (Siman-Tov and Schweitzer 2018, p. 3). When the Palestinian public started to lose interest in weekly protests at the border, became dissatisfied with the number of casualties and lack of political gains, successful arson attacks appeared to be a suitable morale-booster. As the figure below shows, the number of Palestinians interested in weekly protests dropped significantly after the major protest on 14 May. The end of May and beginning of June also marked the first coordinated arson attacks on a much larger scale than before (including fires which burned up to 740 acres of Carmia nature reserve on 2 June 2018)5;
Despite the fact that the incendiary kites and balloons can be perceived as rather primitive weapons, they are difficult to spot and eliminate before they touch the ground. Coordinated, simultaneous attacks conducted in different locations have become a particular challenge to the Israeli army and emergency services. Even though the countermeasures were developed and detection of the arson devices has improved, the Israeli army and emergency services did not have enough means and forces to prevent all the fires at once when the attacks reached momentum in the dry summer season. There is no way to physically block the balloons from coming – they pass over the border barrier easily with the wind;
Airborne devices have been used not only to start fires in the ‘Gaza Envelope’, but also to send IEDs to target the local Israeli population. The border barrier, successfully barring the access of the Palestinian militants to Israeli territory, has so far provided an efficient measure to prevent bombing attacks. The only way for Hamas to reach Israel is through the underground tunnels and it rarely succeeds. The kites and balloons provide a cheap and easy solution to by-pass the border barrier and place IEDs at the Israeli side of the fence with no risk to the militants. There were several reports of IEDs attached to fancy party balloons with cartoon decorations, aimed to attract children. Most of them required IDF or Police sappers to dismantle or detonate safely. Danger to the children maximised fear among local residents and compelled the Israeli authorities to introduce additional safety instructions (Gross 2018a);
Damage to the Israeli farmlands and nature reserves, along with the threat of explosives brought by the kites and balloons, managed to affect the Israeli communities of the ‘Gaza Envelope’. The number of local residents treated for anxiety and Post-Traumatic Stress Disorder has seen an increase since the arson attacks began. Hamas was also able to exploit the frustrations of the Israelis who saw the response of the IDF as insufficient and demanded decisive military retaliation to prolonged rocket barrage and arson attacks. A situation in which the citizens lose their trust in the military and emergency services might pose a serious threat to national security. The escalation of public frustration had an impact on Israeli politics as well and resulted in the resignation of the Israeli Defence Minister, who opposed the Prime Minister’s ceasefire efforts (SimanTov and Schweitzer 2018, p. 3);
Local climate is typified by hot, rainless summers. That enables the fires to spread at fast speed and makes them extremely hard to extinguish. Grasses, bushes and green-woods in the Western Negev catch fire easily in the dry season, which usually extends from early May to October. Climate determinants have been also exploited by Hamas and it shows in the frequency of arson attacks. They started at the beginning of the dry season. In late September, the number of attacks dropped significantly and they were almost completely halted for the rainy winter6 (Tress 2018). As a precise forecast for the wind direction is nowadays available in various free on-line sources, choosing the right moment to launch the kites or balloons is not a difficult task. One could assume that there might have been unexpected changes of the wind direction which resulted in blowback of the incendiary devices, but there were no confirmed Israeli or Palestinian reports of fires started inside the Gaza Strip by the kites and balloons.
Fig. 1
Estimated number of Palestinians participating in the protests along the Gaza-Israeli border in 2018 in juxtaposition with the beginning of mass-scale arson attacks
As indicated above, incendiary kites and balloons are quite primitive, yet dangerous weapons in the hands of a terrorist organizsation. Despite not having caused any human casualties so far, arson attacks at the Israeli-Gaza border have succeeded in creating an atmosphere of constant fear and frustration among local residents and to affect political decisions in Israel. This makes the airborne arson attacks a useful tactic for terrorist purposes, as it provides a way to accomplish two major goals of terrorism: intimidation of societies and impact on governments (see: NATO 2018, p. 124, UNSC 2004). As Kydd and Walter (2006, p. 50) suggest, terrorism works because it causes governments and individuals to respond in ways that aid the terrorists’ cause. In the case of the analysed arson attacks, the Israeli reaction provided Hamas with great material for propaganda purposes: tightening of the blockade of the Gaza Strip and shortage of supplies were portrayed in the media as an act against the Palestinian civilians. This message was aimed mainly at the international public. Both military response to the attacks and restraint of the IDF could be exploited for the cause of Hamas as well. Any air strikes against balloon launchers would allow Hamas to accuse the opponent of disproportionate use of force. As mentioned before, the Israeli army avoided retaliation strikes in response to arson attacks, which was presented to the Palestinian public as a sign of weakness and was exploited by Hamas for internal buildup of support as well as undermined the trust of the Israeli residents of the Gaza periphery in their own army and government. Eventually, the attacks created a stalemate situation in which the Israeli response would always result in adverse effects and would somehow serve the cause of Hamas, regardless of the decision taken.
Israeli countermeasures against airborne arson attacks
Countermeasures against the arson attacks, implemented by the IDF and by the civilian sector, can be divided into three main categories:
Measures that minimise casualties, economic and ecological damage (passive defence);
Tactics and devices used to spot the incendiary kites and balloons and prevent them from sparking fires (active defence);
Preventive measures undertaken to stop the enemy from launching the kites and balloons.
The first category includes all the passive activities, which were implemented to deal with the new threat, such as the deployment of additional fire brigades in the region affected by arson attacks. Soldiers from IDF units in the nearby area were sent to assist the fire-fighting effort too. Volunteer firefighters from non-profit organisations, such as Keren Kayemeth LeIsrael7 and the Emergency Volunteers Project8, were also deployed in the ‘Gaza Envelope’ to support the National Fire and Rescue Services (Keren Kayemeth LeIsrael 2018). Another passive defence measure was early harvesting, promoted by the Agriculture and Finance Ministries. Local farmers, whose fields are located close to the Gaza border, were offered financial compensation in exchange for harvesting crops ahead of July. The intent was to save at least a part of the yield and to reduce the scale of the fires thanks to the removal of dry wheat. This solution, however, generated high expense and was not accepted by all the farmers (Israel Ministry of Foreign Affairs 2018). In order to avoid casualties from airborne IEDs, the Israeli authorities released new safety instructions for the local residents.
Active defence against the arson attacks consists of observation, detection and neutralisation of the incendiary devices. Initially, regular observation drones were deployed by the IDF at the border to spot the incoming kites and balloons. High stationary watch towers have been used, too, in order to search for fires and send tfiremen to the scene. In June 2018, the Israeli army confirmed the deployment of a new tracking system, which uses sensitive optical sensors and command & control software to monitor the sky for up to 10 kilometres. ‘Sky Spotter’, built by Rafael Advanced Defence Systems, was initially designed for the IDF as a countermeasure against small drones coming from the enemy’s territory. It also turned out to be a useful tool for spotting the incendiary kites and balloons, tracking their flight parameters and plotting their likely destination. This allows the IDF operators to notify the firefighters who can arrive on time and extinguish the flames. According to the released information, ‘Sky Spotter’ can also direct small defensive drones to collide with the kites or balloons and bring them down. There were several reports of tested laser devices that could destroy the incendiary kites and balloons in the air (Dvori 2018). It seems that ‘Sky Spotter’ is not the only technological solution, which was originally developed to fight the UAVs, but may be effective against the arson devices. An autonomous UAV system called ‘Goshawk’, which was recently designed by an Israeli high-tech startup RoboTiCan for taking down hostile drones, has also been tested to intercept and neutralise incendiary kites and balloons. It might be deployed at the Gaza border if the arson attacks resume (Israel’s Homeland Security 2018).
Preemptive and preventive countermeasures are perceived in Israel as the most effective solutions against the incendiary kites and balloons, but they also spark the most controversy. There were multiple reports of the IDF firing warning shots near the people who were spotted by the observation drones while preparing to launch balloon clusters. The Israeli Air Force conducted a few direct strikes against Hamas members carrying out arson attacks, who reportedly got injured, but there were no casualties. However, the Israeli authorities rarely authorised the use of firepower to prevent arson attacks. Further escalation and a large-scale confrontation with Hamas were apparently perceived as counterproductive in the current strategic situation. Frequent airstrikes against the balloon launchers could also be perceived as a disproportionate use of force, which would significantly reduce the chances of Israel winning the sympathy of the international community. The noticeable restraint of the Israeli authorities caused disputes among the ruling coalition members and led to personnel changes in the government. It also increased social tensions, as most of the Israelis strongly support military response to the new threat. According to the research conducted by the Israel Democracy Institute in June 2018, over 83% of the Jewish Israeli public was in favour of direct IDF attacks against those who launch the incendiary devices (while 87.5% of the Israeli Arab minority was against such preventive measures) (Yaar and Hermann 2018, p. 1).
Other preventive measures include economic blockade, which was supposed to force Hamas to stop arson attacks due to social pressure in the Gaza Strip. Besides imposing strict control on helium imports, deliveries of other goods were temporarily blocked or limited when the arson attacks reached their momentum. In July 2018, Israel closed the main border crossing in Kerem Shalom to all cargo shipments, except for food, medicines and basic humanitarian supplies. Fuel and gas deliveries were temporarily halted as well, causing serious power shortages and frequent blackouts in the enclave (Efron, Fishbach and Blum 2018, pp. 4–5). The Israeli government also imposed financial penalties on the Palestinian Authority. In June, the Prime Minister announced that Israel was planning to deduct from the tax funds it transfers monthly to the Palestinian Authority in order to compensate the farmers from the Gaza periphery9 (Rosenberg 2018). It was broadly criticised, as the Palestinian Authority officials residing in Ramallah have not had any control over Hamas-ruled Gaza Strip since 2007, so the financial penalty would not affect the actual attackers in any way. It seems that this move was intended to satisfy the Israeli population rather than to prevent arson attacks with economic pressure.
All of the listed countermeasures show that the Israeli advanced defences were in fact challenged by cheap, low-tech arson devices from the Gaza Strip. It seems that the solutions to this new problem are being gradually tested and, with time, they are becoming more efficient. Most of them were developed ad hoc and they will definitely need further improvement if the attacks continue after the rainy season is over in 2019.
Conclusions
Despite being non-lethal, weaponised kites and helium balloons proved to be useful weapons for the goals of terrorist organisations. Paradoxically, Hamas managed to bypass the Israeli high-tech defence system by using the most primitive, ridiculously simple materials and tactics it could acquire in the Gaza Strip. Since the incendiary kites and balloons are easily constructed and much cheaper than any other weapon used by Hamas, they can be launched in large numbers and engage untrained supporters of the organisation, including adolescents. The local climate, especially in the dry summer season, creates perfect conditions for such attacks. Visible results, shown to the Palestinian public, allow Hamas to keep the support of the Gazan residents despite lack of real political successes and this is probably one of the main reasons why this new type of attack has been conducted so frequently. The extent of economic damage caused by arson attacks in Israel should not be exaggerated, as 3 million USD is not substantial on a national scale – however, it should be emphasised that the property losses and protracted disruption of everyday routine had a significant impact on the lives of the ‘Gaza Envelope’ residents and, as a consequence of growing social frustrations, eventually managed to influence the composition of the central government and its decisions.
It can be assumed that if the situation between Israel and Hamas remains unchanged, arson attacks will be renewed in 2019 after the rainy season is over, because none of the sides seems to be willing to compromise. Keeping that in mind, it is very likely that the Israeli army and civilian emergency services will have to work on improvement of the initial countermeasures against the kites and balloons. As indicated in the article, both passive and active defence measures turned out to be only partially effective. Some of the prevention attempts failed to have any impact on the attackers or – as in the case of economic blockade – cannot be used for a longer period of time due to the risk of humanitarian crisis. As experts from the Israeli Institute for National Security Studies suggest, neutralising incendiary kites and balloons is only a tactical issue, while the systemic threat to the Israeli national security that comes from the Gaza Strip requires solutions on the strategic level (Elran and Padan 2018). As long as the problem of the Palestinian Authority division and alienation of the Gazans remains unresolved, successful elimination of the arson attacks would only motivate Hamas to come up with another method of asymmetric warfare.
Airborne arson attacks at the Gaza-Israeli border can be studied as a valuable example of asymmetry in armed conflict. This paper attempted to highlight the fact that the huge economic and technological gap between two sides of the conflict may not always be in favour of the more powerful actor. As the findings of this research show, cheap and simple, but unexpected tactics can become a serious challenge to the well-developed armed forces and emergency services, which require time and a lot of effort to come up with solutions to such threats.




