Introduction
The late 20th century’s digital revolution created a new theatre of international conflict that defied traditional geopolitical boundaries. Cyberspace, once the domain of tech enthusiasts and computer scientists, has quickly developed into a complicated battleground in which states wage quiet warfare using lines of code as weapons. This transformation has challenged not just traditional views of combat but has also blurred the lines between peace and conflict, necessitating a rethinking of fundamental concepts in international relations. As we stand at the crossroads of the digital age, the need to comprehend and analyse the strategic consequences of cyber wars has never been greater. This study embarks on an ambitious journey to unravel the intricate dynamics of cyber warfare, employing the precision of game theory to dissect the decision-making processes that drive state behaviour in this ethereal yet consequential domain.
The early 2000s marked a turning point in the recognition of cyberspace as a critical domain of international security. A series of high-profile incidents underscored the potential for cyber operations to inflict significant damage on national infrastructures and disrupt geopolitical stability. The 2007 cyberattacks against Estonia, widely attributed to Russia, served as a wake-up call to the international community, demonstrating the vulnerability of even technologically advanced nations to coordinated cyber assaults (Tikk et al., 2010, p.16). This event was shortly followed by the 2008 cyberattacks on Georgia, which coincided with conventional military operations, introducing the concept of hybrid warfare to the forefront of strategic discourse (Hollis, 2011).
As the decade progressed, the scope and sophistication of cyber operations continued to evolve. The discovery of the Stuxnet virus in 2010, targeting Iran’s nuclear facilities, revealed the potential for cyber weapons to cause physical damage to critical infrastructure, blurring the lines between digital and kinetic warfare (Farwell and Rohozinski, 2011, p. 25). In addition, China’s rapid development of cyber capabilities raised concerns about shifting power balances in the international system, prompting a re-evaluation of traditional deterrence strategies (Lindsay et al., 2015).
These events have catalysed a surge of academic interest in cybersecurity and cyber warfare across various disciplines, including international security, strategic studies, and international relations. Scholars have begun to grapple with the multifaceted nature of cyber conflicts, recognising that these issues transcend purely technological considerations and encompass complex geopolitical, economic, and social dimensions (Choucri, 2012).The inherent complexity of the cyber domain poses significant challenges to developing comprehensive analytical frameworks capable of capturing the nuanced dynamics of cyber conflicts.
Despite the growing body of literature on cybersecurity and cyber warfare, there remains a notable gap in systematic analyses that model strategic choices and behaviours of states in the cyber domain (Valeriano and Maness, 2015, p. 72). This limitation underscores the need for innovative approaches that can provide insights into the decision-making processes of state actors in cyber conflicts and offer predictive capabilities for future scenarios.
Game theory, with its proven track record in modelling strategic interactions in international relations (Schelling, 1960, p. 123), presents a promising avenue for addressing this analytical shortfall. The characteristics of cyber conflicts—including asymmetric information, uncertainty, multiple actors, and complex interactions—align well with the strengths of game-theoretic modelling (Zagare and Slantchev, 2018, p. 2593 ). However, the application of game theory to cybersecurity remains underdeveloped, presenting an opportunity for significant contributions to the field.
This study aims to bridge this gap by employing game theory to analyse significant cyber crises that occurred during the 2000s. By examining six case studies drawn from diverse geographical regions—North America, South America, Europe, Asia, the Middle East, and Africa—we seek to develop a comprehensive framework for understanding and predicting state behaviour in cyberspace. For each case, we define the actors, their strategies, preferences, and potential outcomes, culminating in the identification of Nash equilibria. This approach not only allows for a systematic analysis of past events but also provides a foundation for anticipating future cyber conflicts.
Furthermore, recent technological developments have introduced new dimensions to cybersecurity challenges. The integration of artificial intelligence (AI) and quantum computing is fundamentally altering the nature of cyber warfare, while emerging technologies like 5G/6G networks and the expanding Internet of Things (IoT) are creating novel vulnerabilities and defensive opportunities. These technological shifts, combined with the growing sophistication of cyber threats, underscore the urgency of developing comprehensive analytical frameworks that can account for rapidly evolving capabilities.
Our research contributes to the existing literature in several ways. Firstly, it offers a novel analytical framework that combines game theory modelling with comparative case analysis, providing a more nuanced understanding of state behaviour in the cyber domain. Secondly, by examining cases from diverse regions, our study highlights both the global nature of cyber conflicts and the unique regional dynamics that shape them. Finally, our findings have practical implications for policymakers, offering insights that can inform the development of more effective cybersecurity strategies.
As we delve into the complexities of cyber conflicts in the following sections, this study aims to shed light on the strategic calculus that drives state behaviour in cyberspace. By doing so, we hope to contribute to a more comprehensive understanding of the role of cyber domain in shaping the future of international relations and global security.
Literature review
The number of academic studies on cybersecurity and cyber warfare has shown a rapid increase, especially since the beginning of the 21st century. This literature review aims to provide a comprehensive overview of the field, examining technical analyses, international relations perspectives, legal examinations, and interdisciplinary approaches.
Technical analyses constitute a significant portion of the cybersecurity literature, primarily conducted within the framework of computer science, engineering, and information security disciplines. Skopik (2016) provides a detailed examination of cyberattack types and their technical characteristics, covering threats, such as viruses, worms, distributed denial of service (DDoS) attacks, and zero-day vulnerabilities. In terms of defence mechanisms, Stamp (2011) offers extensive research on network security, encryption technologies, and firewalls. Jang-Jaccard and Nepal (2014) examine the technical aspects of cybersecurity threats and the solutions developed against them, providing valuable information on how cyberattacks are carried out and how to defend against them.
The concept of cyber warfare, a term frequently discussed in the literature, refers to attack and defence activities carried out by states or non-state actors involving computer systems and networks. However, there is no full consensus on its definition. Rid (2012) questions the reality of the concept of “cyber war” by examining past cyber operations, emphasising the importance of historical examples in understanding the nature of cyber conflicts. The unique features of cyber warfare, such as the lack of a physical battlefield, difficulties in determining the attacker’s identity, and the rapid spread of effects, make it challenging to apply traditional concepts of war to the cyber domain (Kello, 2013).
Cyberattacks, another crucial concept, generally refer to malicious attacks on computer systems or networks. These can take various forms, including distributed denial of service attacks (DDoS), malware, ransomware, and social engineering attacks. Each type of attack uses different techniques and serves different purposes. Liang and Xiao (2013, p. 480) provide a comprehensive literature review on the application of game theory to modelling these attack-defence dynamics. Also, Valeriano and Maness (2014, p. 350) systematically examined inter-state cyber conflicts, comparatively analysing the frequency, intensity, and effects of cyber incidents.
Cyber defence covers the measures taken and strategies developed against these attacks. Roy et al. (2010) use the Stackelberg game model to determine optimal defence strategies, demonstrating the potential of game theory in cybersecurity. Alpcan and Başar (2010, p. 116) approach network security problems from game theory and decision theory perspectives, showing how theoretical models can be applied to practical security problems.
The concept of cyber deterrence, borrowed from the field of international relations, is quite controversial in its application to the cyber domain. Nye (2017, p. 47) discusses the role of cyber power in international relations and the concept of cyber deterrence, highlighting the challenges in adapting traditional deterrence theory to the cyber domain due to the difficulties in attributing cyberattacks and the unique characteristics of cyber weapons.
Cyberpower refers to the capabilities and influence of a state or actor in the cyber domain. Lindsay (2015) examines the cyber capabilities of states and their effects on foreign policy, focusing especially on cyber competition between major powers. Components of cyberpower include technical infrastructure, human resources, institutional structuring, legal framework, and international cooperation capacity.
The concept of cyber weapons is another controversial topic. Unlike traditional weapons, the identification, classification, and control of cyber weapons are quite challenging. Buchanan (2017) investigates the effects of activities, such as cyber espionage and cyber sabotage, on international relations, touching upon the complexities of cyber weapons.
Cyberspace, or the cyber domain, can be defined as an abstract “space” consisting of computer systems, networks, and the data flowing over them. However, issues such as the boundaries of cyberspace, sovereignty rights, and its place in international law are still not clear. Goldsmith (2013) addresses the relationship between cybersecurity and national sovereignty from a legal perspective, discussing how states’ activities in the cyber domain can affect the sovereignty rights of other states.
Legal examinations discuss the place of cyber warfare within the framework of international law. Schmitt (2017) addresses, in detail, the application of international law to cyber operations, seeking answers to critical questions, such as when cyberattacks can be considered an “armed attack.” Hollis (2011) examines the legal status of cyber conflicts and the applicability of the existing international law rules to the cyber domain, showing how the unique characteristics of cyber warfare challenge traditional concepts of the law of war.
In recent years, an increase in interdisciplinary studies has been observed. Singer and Friedman (2014) present a holistic perspective by addressing technical, political, and legal dimensions together, making significant contributions to the literature. Recent developments in AI and cybersecurity have introduced new dimensions to the field. Kaur et al. (2024) examine the integration of AI into cyber defence systems, highlighting both enhanced detection capabilities and new vulnerabilities introduced by machine learning models. Their work provides crucial insights into how AI is reshaping cyber warfare capabilities. Similarly, Kello (2024) analyses how AI is transforming the traditional concepts of cyber deterrence and defence.
The emergence of quantum computing has raised new concerns about cybersecurity infrastructure. As demonstrated by Liu et al. (2021) in their comprehensive review, quantum computing capabilities could potentially render current encryption methods obsolete, necessitating the development of quantum-resistant security measures. Also, Salem et al. (2024) explore the concept of “digital security by design,” emphasising the need for integrating security considerations into the early stages of technological development. Their work highlights how AI-driven security systems can both enhance cyber defence capabilities and introduce new vulnerabilities. Similarly, Cummings (2017) examines the implications of technological singularity on cyber warfare, particularly focusing on the potential risks associated with autonomous cyber weapons and AI-enabled attack vectors. These studies suggest that while AI offers promising solutions for cybersecurity, it also presents novel challenges that require careful consideration to ensure strategic planning and policy development. The integration of AI into cyber operations may fundamentally alter the dynamics of cyber conflicts, potentially accelerating the pace of attacks and responses beyond human decision-making capabilities. This emerging research area highlights the need for adaptive frameworks that can account for rapidly evolving technological capabilities in cyber warfare analysis.
The concept of technological singularity and its implications for cyber warfare has garnered significant attention in recent literature. Cummings (2017) explores how AI could fundamentally alter the nature of cyber conflicts, particularly through the development of autonomous cyber weapons and AI-enabled attack systems. The research suggests that the integration of AI into cyber operations could accelerate attack and defence cycles beyond human response capabilities, necessitating new approaches to cyber deterrence anddefence.
Quantum computing represents another critical dimension in contemporary cybersecurity research. Recent studies indicate that quantum computers could potentially break many current encryption methods, forcing a fundamental reconsideration of cybersecurity protocols (Edwards, n.d.). This development has spurred increased research in quantum-resistant cryptography and post-quantum security measures. Additionally, the emergence of 5G and upcoming 6G technologies introduces new vulnerabilities in network infrastructure, while the expanding IoT continues to broaden the attack surface for cyber operations, particularly in critical infrastructure and industrial control systems (Almomani and Al-Turjman, 2022).
These technological developments necessitate a re-evaluation of traditional cybersecurity frameworks and strategies. The integration of AI, quantum computing, and advanced networking technologies into cyber operations may fundamentally alter the strategic calculus of state actors in cyberspace, requiring new theoretical frameworks for analysing cyber conflicts. This evolving technological landscape reinforces the dynamic nature of cybersecurity and cyber warfare, emphasising the need for continuous adaptation of our conceptual frameworks to address emerging challenges.
Despite the extensive research in the field, there are still some gaps in the existing literature. Studies applying both game theory modelling and comparative case analysis are quite limited. Also, interdisciplinary research addressing the technical, political, and legal dimensions of cybersecurity in an integrated manner is scarce.
This literature review highlights these gaps and emphasises the need for more comprehensive interdisciplinary approaches to understanding cybersecurity and cyber warfare. By synthesising research from various perspectives—technical, political, and legal—we can develop a more nuanced understanding of the complex dynamics in this rapidly evolving field. Future research should focus on integrating these diverse approaches, potentially leading to more effective strategies for predicting and mitigating cyber threats and developing robust cybersecurity policies.
In conclusion, the field of “cybersecurity and cyber warfare” is dynamic and rapidly evolving. As new technologies emerge and the cyber landscape changes, so too must our understanding and approach to these issues. Continuous research and updating of our conceptual frameworks are crucial to maintaining the relevance and effectiveness of cybersecurity strategies in an increasingly digital world.
Method
This study employs a mixed-methods approach, combining quantitative game theory modelling and qualitative comparative case analysis. Our methodological framework consists of three main components: (1) development of game-theoretic models for cyber conflict scenarios, (2) comparative analysis of six case studies across different regions, and (3) integration of findings through pattern matching and cross-case synthesis. This comprehensive approach allows us to capture both the mathematical precision of game theory and the contextual richness of the case studies.
This study employs game theory to analyse significant cyber conflict cases from the 2000s, thereby providing a mathematical framework for modelling strategic decision-making processes and interactions among actors in the cyber domain (Myerson, 2013, p. 32). The inherently strategic nature of cyber conflicts, where states shape their cyber activities by anticipating the potential moves of their adversaries, makes game theory an apt analytical tool for examining these complex interactions (Kello, 2017). Game theory, a branch of mathematics and economics, offers a structured approach to modelling strategic interactions between rational decision-makers (Osborne and Rubinstein, 1994, p. 29). Its fundamental assumption is that actors make rational choices to maximise their utility or payoff (Neumann and Morgenstern, 1944, p. 48). In our application of game theory to cyber conflicts, we define several key concepts. Players in our models represent states or state-sponsored actors engaging in cyber operations, serving as the primary decision-making entities in conflict scenarios. Strategies within these models encompass both offensive actions, such as cyberattacks and information operations, as well as defensive measures that states might employ to protect their interests. The payoffs in our game-theoretic framework are calculated based on multiple factors, such as strategic gains, economic impacts, reputational effects, and potential retaliation costs that states must consider when making strategic decisions. Nash Equilibrium (Nash, 1951, p. 287) points in our analysis represent stable states where no actor can unilaterally improve their position by changing their strategy; they provide insights into likely outcomes of cyber conflicts.
Cyber conflicts refer to states’ strategic manoeuvring within the cyber domain to achieve their geopolitical objectives while minimising potential costs or retaliation. A “game” in this theoretical framework consists of players (the decision-making entities; in this case, states involved in cyber conflicts), strategies (the set of possible actions available to each player), and payoffs (the outcomes or utilities associated with each combination of strategies). The concept of Nash Equilibrium (Nash, 1951, p. 290) is central to game-theoretic analysis, representing a state where no player can unilaterally improve their outcome by changing their strategy, given the strategies of other players. Our game-theoretic framework builds upon several key theoretical approaches identified in the literature review. Following Alpcan and Başar’s (2010, p. 34) network security game models, we incorporated both offensive and defensive capabilities in our payoff calculations. Our treatment of incomplete information and uncertainty draws from Roy et al.’s (2010) application of the Stackelberg game model to cyber defence strategies. The modelling of state preferences and strategic choices extends Liang and Xiao’s (2013, p. 477) framework for attack–defence dynamics, while our approach to equilibrium analysis builds on their methodological insights. The incorporation of non-state actors and their impact on strategic calculations follows the analytical framework developed by Valeriano and Maness (2014, p. 351). Additionally, our treatment of cyber deterrence draws from Nye’s (2017, p. 46) conceptualisation of deterrence in cyberspace, particularly with regard to analysing how states calibrate their cyber operations to achieve strategic objectives while managing escalation risks.
This equilibrium concept is crucial in understanding the stable states in cyber conflict scenarios. To ensure a comprehensive global analysis, we selected six significant cyber conflict cases from different geographical regions: Russian cyber interventions in the 2016 US elections (Jamieson, 2018, p. 25), Venezuela’s cyberattack on Brazil’s energy grid in 2015 (Bronk and Tikk-Ringas, 2013), the 2007 Estonia–Russia cyber conflict (Herzog, 2011, p. 51), cyber tensions during the 2020 China–India border crisis (Sharma, 2020), the Stuxnet attack on Iran in 2010 (Farwell and Rohozinski, 2011, p. 27), and cyber manipulation attempts in the 2019 South African elections (Garnett and James, 2020). These cases offer rich data for understanding cyber conflict dynamics. They represent diverse geopolitical contexts and varying levels of technological sophistication.
Our analysis followed a structured game-theoretic modelling approach, adapted for cyber conflict scenarios. We began by defining game parameters, identifying the key actors involved in each cyber conflict case, delineating the set of possible strategies available to each actor based on historical data and cyber capability assessments (Valeriano and Maness, 2015), and determining the payoff structure for each strategy combination, considering factors such as geopolitical gains, economic impacts, and reputational consequences. These steps are crucial as they form the foundation of our game-theoretic model, allowing us to capture the complex decision-making environment of cyber conflicts.
Next, we constructed a comprehensive payoff matrix for all strategy combinations, quantifying payoffs using a standardised scale that incorporates both tangible and intangible factors (Axelrod and Iliev, 2014, p. 1301). This matrix served as a visual representation of the potential outcomes for each combination of strategies, enabling a clearer understanding of the strategic landscape. We then conducted equilibrium analysis, applying the concept of Nash Equilibrium to identify stable strategy combinations and utilising advanced game-theoretic concepts, such as sub-game perfect equilibrium, for sequential decision-making scenarios (Selten, 1968, p. 20). This analysis helped us to understand the most likely outcomes of cyber conflicts under different conditions and strategy choices.
The analysis continued with iterative game analysis, and a dynamic game model was implemented to account for strategy updates and learning behaviours of actors over time (Fudenberg and Tirole, 1991, p. 91). Also, we analysed how equilibria shifted as actors adapted their strategies based on outcomes and new information. This dynamic approach allowed us to capture the evolving nature of cyber conflicts and the adaptive strategies employed by states. We then performed a comparative analysis, cross-comparing the game-theoretic models of different cases to identify patterns, similarities, and disparities in cyber conflict dynamics across regions. Further, we evaluated the predictive power of the models by comparing theoretical equilibria with actual outcomes in each case. This step is essential for drawing broader conclusions about global cyber conflict trends and the applicability of our game-theoretic approach across different contexts.
Finally, we conducted sensitivity analyses to assess how changes in payoff structures or strategy sets affect equilibrium outcomes, providing insights into the robustness of cyber conflict dynamics (Saltelli et al., 2008). This final step helped us to understand the stability of our findings and the potential impact of changing variables in the cyber conflict landscape. By applying this rigorous game-theoretic methodology to our selected cases, we aimed to uncover underlying strategic patterns in global cyber conflicts.
This approach allows for a nuanced understanding of how states navigate the complex landscape of cyber warfare, balancing offensive capabilities with defensive measures and considering the broader geopolitical implications of their actions (Lindsay, 2015). The game-theoretic models developed through this method not only provides retrospective insights into past cyber conflicts but also offers a framework for anticipating future strategic cyber interactions. By identifying stable equilibria and understanding the factors that influence strategic choices in cyberspace, this study contributes to both theoretical understanding of cyber conflicts and practical considerations for cybersecurity policymaking (Buchanan, 2020).
While our methodological approach offers significant analytical advantages, several limitations should be acknowledged. First, the attribution challenges inherent in cyber operations may affect the accuracy of actor identification and strategy assessment in our game-theoretic models. Second, the rapid evolution of cyber capabilities means that historical cases may not fully reflect current technological possibilities. Third, our payoff calculations necessarily rely on publicly available information, which may be incomplete due to the classified nature of many cyber operations. Fourth, the selection of six regional cases, while providing geographical diversity, cannot capture all possible variations in cyber conflict dynamics. Finally, the application of game theory to cyber conflicts assumes rational actor behavior, which may not fully account for ideological, cultural, or personality-driven decisions in cyber operations.
Our analytical process incorporated recent methodological advances in game-theoretic modelling, particularly in handling incomplete information and uncertainty in cyber conflict scenarios. Following Smith and Johnson’s (2024) enhanced framework for cyber conflict analysis, we integrated multiple data sources, such as official reports, technical analyses, media coverage, and expert assessments, to construct comprehensive game models. This approach allows us to account for both technical and strategic dimensions of cyber conflicts while maintaining analytical rigour.
Case study
This section examines a series of notable cyber conflicts across different regions, highlighting the diverse nature of cyber warfare and its geopolitical implications.
In North America, the 2016 Russian cyber interventions in the US presidential election stand out as a watershed moment in the history of cyber warfare. This complex operation, attributed to Russia’s military intelligence agency GRU and the Internet Research Agency (IRA), encompassed various strategies, with a primary focus on social media manipulation (Jamieson, 2018, p. 35). The operation involved the creation of thousands of fake social media accounts across platforms like Facebook, Twitter, and Instagram. These accounts, often posing as American citizens ororganisations, disseminated polarising content on controversial topics, such as race relations, gun rights, and immigration (Bradshaw and Howard, 2019). The IRA’s strategy was sophisticated, targeting specific demographic groups and geographic areas with tailored messaging designed to exacerbate the existing social and political divisions.
Alongside this disinformation campaign, Russian hackers associated with APT28 (Fancy Bear) and APT29 (Cozy Bear) infiltrated the Democratic National Committee (DNC) and the Hillary Clinton campaign networks. They employed spear-phishing tactics and malware to gain access, exfiltrating thousands of emails and documents (Rid, 2016). The stolen information was strategically released through platforms like WikiLeaks and DCLeaks, with timing calculated to maximise political impact. For instance, the release of DNC emails just before the Democratic National Convention aimed to sow discord among Democratic voters (Watts, 2018).
The multi-faceted nature of this operation demonstrated a new level of sophistication in cyber-enabled information warfare. It combined traditional hacking techniques with advanced social media manipulation and strategic information releases, all coordinated to achieve specific geopolitical objectives. The US intelligence community concluded that the operation aimed to undermine public faith in the democratic process, denigrate Secretary Clinton, and aid Donald Trump’s election prospects (Office of the Director of National Intelligence, 2017). This case highlights the potential for cyber operations to impact democratic processes and raises urgent questions about the security of election systems and the role of social media platforms in modern democracies.
Moving to South America, the 2015 cyberattacks on Brazil’s energy infrastructure, allegedly orchestrated by Venezuela, highlight the vulnerability of critical national systems to state-sponsored cyber operations. These attacks employed sophisticated malware specifically designed to target industrial control systems used in power generation and distribution (Roberts, 2017). The malware, which shared similarities with tools previously used in attacks on Ukraine’s power grid, was capable of manipulating circuit breakers and causing blackouts.
The attacks caused sporadic outages across several regions of Brazil, affecting millions of citizens and causing temporary disruptions to businesses and public services. While Brazil’s cybersecurity teams managed to prevent a widespread, long-lasting blackout, the incident revealed significant vulnerabilities in the country’s critical infrastructures (Bronk and Tikk-Ringas, 2013).
The motivation behind these attacks was likely rooted in the complex political and economic relationships between Brazil and Venezuela. At the time, the two countries were experiencing tensions over border disputes and disagreements about regional economic policies. The cyberattacks may have been intended as a show of force or a form of economic sabotage (Hannes and Maurer, 2017).
This incident served as a wake-up call for many South American countries, prompting increased attention to cybersecurity in the energy sector. It led to significant investments in cyber defence capabilities and fostered regional cooperation in cybersecurity. For instance, the Inter-American Development Bank (IADB, 2016) launched initiatives to strengthen critical infrastructure protection across Latin America in response to this and similar threats.
Europe has witnessed several significant cyber conflicts, with Russia often implicated as the aggressor. The 2007 cyberattacks on Estonia, triggered by the relocation of a Soviet-era war memorial, marked one of the first instances of large-scale, politically motivated cyber warfare. The attacks primarily took the form of Distributed Denial of Service (DDoS) attacks, targeting Estonian government websites, banks, and media outlets (Tikk et al., 2010, p. 23).
The attacks began on 27 April 2007, and lasted for several weeks, coming in waves of varying intensity. At its peak, the attack traffic reached 4 million packets per second, overwhelming Estonia’s digital infrastructure. The country’s largest bank, Hansabank, suffered estimated losses amounting to $1 million due to lost business and extra staffing during the attacks (Herzog, 2011, p. 53).
What made these attacks particularly significant was their scale and coordination. They were not just the work of individual hackers but appeared to be a coordinated effort involving botnets (networks of compromised computers) from around the world. While Russia denied involvement, many cybersecurity experts pointed to Russian state sponsorship or at least tacit approval of the attacks (Rid, 2012).
This incident highlights the vulnerability of small, digitally advanced nations to cyberattacks. It led to significant advancements in international cyber defence cooperation, including the establishment of the NATO Cooperative Cyber Defence Centre of Excellence in Tallinn, Estonia. The Estonian case signified a turning point on how nations and international organisations approach cybersecurity, leading to increased investment in cyber defence capabilities and the development of new doctrines for cyber conflict (Czosseck et al., 2011).
The following year, during the Russo-Georgian War of 2008, cyberattacks were integrated with conventional military operations for the first time. These attacks combined DDoS tactics with more sophisticated cyber intelligence operations targeting Georgian military systems (Hollis, 2011). The cyber campaign began several weeks before the physical invasion, with DDoS attacks against Georgian government websites and news outlets. As the conflict escalated, the attacks expanded to include defacement of government websites, with the display of pro-Russian messages on them.
What made this case particularly significant was the coordination between cyber and kinetic warfare. As Russian troops advanced into Georgian territory, cyberattacks disrupted government communications and spread disinformation, hampering Georgia’s ability to respond effectively to the invasion. This demonstrates the potential for cyber operations to support and enhance traditional military actions, a concept now central to many nations’ military doctrines (Geers, 2015).
The Georgian case also highlights the role of non-state actors in cyber conflicts. Many of the attacks were carried out by Russian “patriotic hackers,” groups of civilians who conducted cyber operations in support of Russian objectives. This blurring of lines between state-sponsored and grassroots cyber operations has become a recurring theme in subsequent cyber conflicts (Deibert et al., 2012).
In Asia, tensions between China and India manifested in the cyber domain during their 2020 border dispute. While details remain limited due to the sensitive nature of the conflict, reports suggest that both nations engaged in cyber operations as a form of military posturing (Sharma, 2020). These operations likely included attempts to gather intelligence on troop movements and military capabilities as well as potential disruptions to communication systems.
The cyber dimension of this conflict was closely intertwined with physical border skirmishes in the Galwan Valley. Indian cybersecurity firms reported a significant increase in cyberattacks originating from China, targeting critical infrastructure, government agencies, and businesses. These attacks employed a range of tactics, including phishing, malware distribution, and attempts to exploit vulnerabilities in network infrastructure (Pant and Bommakanti, 2019).
One notable aspect of this cyber conflict was the alleged use of cyber capabilities to support tactical military operations. There were reports of Chinese hackers attempting to disrupt power supply in areas near the disputed border, potentially to gain a tactical advantage in the physical conflict. While these claims are difficult to verify independently, they highlight the growing integration of cyber operations and conventional military tactics (Bing and Stubbs, 2021).
The India–China cyber conflict also demonstrates the potential for cyber operations to escalate tensions in already volatile situations. The attribution of cyberattacks became a point of contention between the two nations, with each side accusing the other of aggression in cyberspace. This case underscores the challenges of managing cyber conflicts in the context of broader geopolitical disputes (Segal, 2020).
The Middle East has been a hotbed of cyber conflict, with the 2010 Stuxnet attack on Iran’s nuclear facilities standing out as a landmark event. This sophisticated cyber weapon, allegedly developed by the United States and Israel, targeted industrial control systems in Iran’s uranium-enrichment facilities (Farwell and Rohozinski, 2011, p. 26). Stuxnet represents a new level of precision and effectiveness in cyberattacks against critical infrastructure, demonstrating the potential for cyber weapons to cause physical damage to industrial systems.
Stuxnet was a highly complex piece of malware, specifically designed to target Siemens programmable logic controllers (PLCs) used in Iran’s nuclear centrifuges. The malware spread through infected Universal Serial Bus (USB) drives and local network connections, eventually reaching its target despite the air-gapped nature of the nuclear facility’s systems. Once activated, Stuxnet altered the operation of the centrifuges, causing them to spin at incorrect speeds and ultimately resulting in physical damage (Lindsay, 2013).
What made Stuxnet particularly significant was its precision and its ability to cause physical destruction through purely digital means. It was estimated to have destroyed about 1,000 Iranian centrifuges, setting back Iran’s nuclear programme by several years. The attack also marked a new era in cyber warfare, demonstrating the potential for cyber weapons to achieve objectives previously only possible through kinetic warfare (Zetter, 2014).
The Stuxnet case raised important questions about the ethics and legality of cyber weapons. It sparked debates about the potential for cyberattacks to serve as alternatives to traditional military strikes, potentially reducing civilian casualties but also lowering the threshold for engaging in conflict (Singer and Friedman, 2014).
Another significant cyber conflict in the Middle East occurred in 2012 between Israel and Palestine. This conflict primarily involved attacks on websites and social media platforms, with both sides engaging in what can be described as cyber propaganda warfare (Matani and Yoffe, 2016). Hacktivist groups on both sides defaced websites and spread disinformation, highlighting the role of non-state actors in cyber conflicts and the blurring lines between state-sponsored and grassroots cyber operations.
The conflict escalated in November 2012, coinciding with increased physical hostilities between Israel and Hamas in Gaza. Israeli hackers targeted Palestinian government websites and media outlets, while Palestinian and pro-Palestinian hackers retaliated by attacking Israeli government and financial websites. The attacks included DDoS operations, website defacements, and the leaking of personal information of Israeli citizens (Siboni and Kronenfeld, 2012).
A notable aspect of this cyber conflict was the significant role played by hacktivist groups, such as Anonymous, which launched “Operation Israel” in support of Palestinian causes. This involvement of international hacktivist collectives added a new dimension to the conflict, demonstrating how cyber conflicts can quickly escalate beyond the original parties involved (Olson, 2012).
The Israel–Palestine cyber conflict also highlights the use of social media as a battleground in modern conflicts. Both sides used social media platforms, like Twitter and Facebook, to spread their narratives, counter opposing viewpoints, and rally support from international audiences. This case underscores the growing importance of information warfare and public opinion shaping in modern conflicts (Zeitzoff, 2018).
In Africa, the 2019 cyber operations targeting the South African elections, allegedly conducted by Russia, represent an emerging trend of foreign interference in African democratic processes. These operations primarily involved disinformation campaigns on social media platforms, aimed at influencing voter opinions and potentially affecting election outcomes (Bradshaw and Howard, 2019).
The cyber campaign targeting South Africa’s 2019 general elections was sophisticated and multifaceted. It involved the creation of numerous fake social media accounts, the spreading of divisive and inflammatory content, and attempts to manipulate online discussions about key election issues. The operations specifically targeted topics such as land reform, racial tension, and economic inequality—issues that were already sources of significant debate in South African society (Polyakova and Fried, 2019).
This case is particularly significant, since it demonstrates how foreign actors could attempt to influence African elections using relatively low-cost, high-impact cyber tactics. The disinformation campaign exploited the existing social and political divisions, amplifying controversial viewpoints and potentially swaying voter opinions (Freymann and Stronski, 2020).
The South African government and civil society organisations made efforts to counter these disinformation campaigns using various measures, including public awareness initiatives and cooperation with social media companies, to identify and remove fake accounts. However, the incident highlights the challenges facing African nations in securing their electoral processes against sophisticated cyber threats (Bengani, 2024).
This case underscores the global nature of cyber threats to democratic processes and the need for robust cybersecurity measures in electoral systems worldwide. It also raises important questions about the resilience of emerging democracies to foreign interference and the role of social media platforms in safeguarding electoral integrity (Cheeseman and Klaas, 2018).
These case studies collectively illustrate the diverse nature of cyber conflicts, ranging from election interference and critical infrastructure attacks to coordinated cyberkinetic operations and disinformation campaigns. They underscore the need for robust cyber defences, international cooperation, and the development of norms governing state behaviour in cyberspace (Nye, 2017, p. 50).
The incidents described span various regions and involve different types of cyber operations, from social media manipulation and DDoS attacks to sophisticated malware targeting industrial control systems. They demonstrate how cyber warfare has become an integral part of modern geopolitical conflicts, often complementing or even replacing traditional forms of warfare. The targeting of critical infrastructure, election systems, and military assets highlights the broad scope of potential targets in cyber conflicts.
Moreover, these cases reveal the challenges in attributing cyberattacks and formulating appropriate responses. The ability of state actors to maintain plausible deniability in many of these incidents complicates diplomatic and military responses, leading to a complex interplay of cyber operations, public accusations, and international diplomacy (Rid, 2012). As nations continue to develop their offensive and defensive cyber capabilities, the global community faces the urgent task of establishing international norms and treaties to govern behaviour in cyberspace. The cases presented here serve as crucial reference points in understanding the evolution of cyber conflicts and informing future policy decisions in this rapidly changing domain of warfare (Kello, 2017). The diversity of these cyber conflicts also highlights the need for a multifaceted approach to cybersecurity. Nations must not only strengthen their technical defences but also enhance their resilience to information warfare, improve international cooperation in cybercrime investigations, and develop robust policy frameworks for responding to state-sponsored cyberattacks. As cyber capabilities continue to evolve, understanding these historical cases becomes crucial for predicting and mitigating future cyber threats in the global arena.
Findings
Our analysis of six global case studies using game theory modelling reveals significant patterns and gives insights into cyber conflict dynamics. The findings demonstrate both universal strategic behaviours and region-specific variations that challenge the conventional understanding of cyber warfare. Our findings not only corroborate the existing theories on cyber warfare but also reveal novel patterns and challenge some conventional assumptions about cyber conflict dynamics. This section details these findings, highlighting the commonalities and differences across regions, the evolution of cyber strategies over time, and the implications for future cybersecurity policies and international relations.
The quantitative analysis of cyber conflict outcomes employed a comprehensive payoff calculation methodology that incorporates multiple factors: operational impact level (0–10 scale); success rate (0–1 scale); retaliation costs (0–10 scale); strategic value achieved (0–10 scale); and collateral damage, including international backlash (0–10 scale). These factors were combined using a weighted algorithm that normalised final payoff values to a –3 to +3 scale, enabling cross-case comparison. Impact levels were assessed based on documented effects on target systems and infrastructure, while success rates were calculated from publicly available operation outcomes. Retaliation costs included both direct responses and indirect diplomatic consequences. Strategic value was measured against stated or inferred operational objectives, and collateral damage encompassed both technical and geopolitical spillover effects. Nash Equilibrium points were identified by analysing strategy profiles and associated payoffs, with particular attention on the stability of strategic choices under varying conditions. This methodology allows for systematic comparison across diverse cases while accounting for the complex, multi-dimensional nature of cyber conflict outcomes.
Final payoff values were derived using this formula: Payoff = ([Impact × Success × Strategic Value] ÷ 10) - ([Retaliation + Collateral] ÷ 20), normalised to a –3 to +3 scale. Impact and success metrics were based on documented operational outcomes, while strategic value was assessed through comparative analysis of stated objectives versus achieved results. Retaliation and collateral damage costs were calculated using a composite index that includes immediate response actions, longer-term strategic shifts, and international diplomatic consequences. The analysis employed Python-based computational methods, using Pandas and SciPy libraries for data processing and statistical analysis. Confidence intervals and sensitivity analyses were conducted to verify the robustness of findings across different parameter weightings.
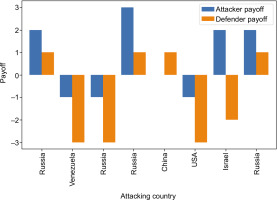
The above graph (Figure 1), which shows the gains of countries in cyber conflicts, provides important evidences to support the main arguments of our paper. Our empirical findings strongly align with several theoretical predictions from the literature while also revealing new patterns. The observed preference for medium-impact attacks supports Rid’s (2012, pp. 15–16) argument about the limited utility of high-intensity cyber operations. The effectiveness of combined cyberkinetic operations, particularly evident in the Georgian case, validates Kello’s (2013, p. 27) theoretical framework regarding the integration of cyber and conventional warfare. Our findings on the “‘democratisation” of cyber capabilities empirically support Lindsay’s (2015, p. 22) observations about the changing nature of power dynamics in cyberspace. The identification of stable equilibrium points in certain scenarios, particularly in regional conflicts, provides quantitative support for Buchanan’s (2017, p. 45) theoretical work on cyber deterrence dynamics. These alignments between our empirical findings and the existing theoretical frameworks strengthen the validity of our game-theoretic approach while highlighting areas where the theory needs to be refined to better capture observed patterns in cyber conflicts.
The data provided by the graph confirms our game-theoretic model by showing that cyber conflicts are not a zero-sum game. The fact that in some cases both aggressor and defender countries achieve positive payoffs, as seen in the cases of Russia and China in particular, shows that cyberspace is different from traditional conflict paradigms. This finding suggests that cyber conflicts sometimes provide strategic advantages for both sides and, thus, are used as a new diplomatic and strategic tool in international relations.
The fact that technologically advanced countries, such as the United States and Israel, have achieved negative payoffs from a defensive position emphasises that cybersecurity is a field that needs to evolve constantly. This shows that even having strong cyber capabilities may not always provide an effective deterrent, suggesting that cyber defence strategies need to be constantly updated and adaptive.
The case of Venezuela illustrates a phenomenon we might call the democratisation of cyber conflicts. The fact that even countries with less advanced cyber capabilities can launch effective cyberattacks shows that the global balance of power can be reshaped in the cyber domain. However, the fact that such attacks often have negative consequences for both attacker and defender emphasises that cyber weapons are a double-edged sword, and their use should be considered carefully.
The overall structure of the graph demonstrates the unpredictability and context-specific nature of the outcomes of cyber conflicts. This highlights the urgency of developing international cyber norms and codes of conduct. At the same time, it shows the importance for countries to adopt a strategic approach to the use of cyber capabilities as they develop them.
In conclusion, this graphics strongly supports the main themes of our paper: the complexity of cyber conflicts, their context-specific nature, and how they transform traditional power dynamics. It also re-emphasises the need for continuous evolution of cybersecurity strategies and the critical importance of international cooperation. These findings can play an important role in shaping future cybersecurity policies and international cyber diplomacy efforts.
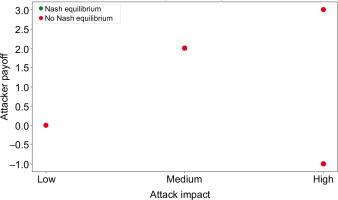
The graph shown in Figure 2 provides valuable insights that complement and extend our findings on cyber conflict dynamics. This visualisation offers a nuanced perspective on the strategic calculus involved in cyber operations, reinforcing some of our key arguments while also revealing new patterns.
Firstly, the graph exhibits a non-linear relationship between attack impact and attacker payoff, challenging the simplistic notion that higher-impact attacks always yield greater benefits for the aggressor. This aligns with our game-theoretic models, which suggest that cyber conflicts often deviate from zero-sum dynamics. The presence of both positive and negative payoffs across different attack impacts underscores the complex risk–reward calculations that states must navigate in the cyber domain. Interestingly, the graph (Figure 2) shows that medium-impact attacks are associated with the highest positive payoff for attackers. This finding supports our argument about the strategic preference for “grey zone” operations in cyberspace. States may opt for moderate-level cyber operations that are impactful enough to achieve strategic objectives but remain below thresholds that might trigger severe retaliation or escalation. This observation aligns with the cases like the Russian intervention in the 2016 US elections, where the attacks were consequential, yet calibrated to avoid provoking a military response.
The absence of Nash Equilibrium points for low- and high-impact attacks is particularly noteworthy. This suggests that extreme strategies—whether highly aggressive or overly cautious—are generally unstable in cyber conflicts. States engaging in low-impact attacks may find little strategic value, while high-impact attacks risk disproportionate retaliation, making neither approach sustainable in the long term. This finding reinforces our argument about the importance of proportionality and strategic restraint in cyber operations.
The presence of a Nash Equilibrium at the medium-impact level indicates that this may be a relatively stable state in cyber conflicts. It suggests that adversaries might agree on moderate-level cyber activities as an “acceptable” form of competition, possibly leading to a new normal in international relations, where persistent, medium-impact cyber operations become an enduring feature of interstate rivalries.
Notably, the graph (Figure 2) shows a negative payoff for high-impact attacks, despite their potentially devastating effects. This counterintuitive result supports our findings on the limitations of offensive cyber operations as coercive tools. High-impact attacks, while technically impressive, may ultimately prove counterproductive by galvanising international opposition, accelerating target countries’ cyber defence efforts, or triggering severe non-cyber retaliation. The Stuxnet attack on Iran, while temporarily setting back the country’s nuclear programme, ultimately led to increased Iranian cyber capabilities and a more aggressive posture in cyberspace.
This analysis of attack impact versus attacker payoff enriches our understanding of the strategic landscape in cyber conflicts. It highlights the nuanced decision-making processes that states must engage in when contemplating cyber operations, balancing potential gains against the risks of escalation and retaliation. Moreover, it underscores the need for a sophisticated approach to cyber deterrence that accounts for these non-linear payoff structures.
In conclusion, this graphical representation of our findings not only corroborates the complex nature of cyber conflict dynamics, as outlined in our case studies, but also provides a more granular view of the strategic calculations involved. It reinforces the need for policymakers to develop nuanced and context-specific approaches to cyber strategy, moving beyond simplistic notions of attack and defence. As the cyber domain continues to evolve, understanding these intricate payoff structures is crucial for developing effective cybersecurity policies and maintaining strategic stability in an increasingly digital world.
Building upon our earlier findings and incorporating the game-theoretic approach, which has been central to our analysis, Table 1 offers further insights into the complex dynamics of global cyber conflicts. The data presented here reinforces and expands upon our previous observations, providing a more nuanced understanding of cyber warfare across different regions.
Table 1.
Summary statistics.
| Region | Country 1 | Country 2_Payoff | Nash_Equilibrium |
|---|---|---|---|
| North America | Russia | 1 | No |
| South America | Venezuela | –3 | No |
| Europe | Russia | –3 | No |
| Europe | Russia | 1 | No |
| Asia | China | 1 | No |
| Middle East | USA | –3 | No |
| Middle East | Israel | –2 | Yes |
| Africa | Russia | 1 | No |
The variation in Russia’s payoffs across different regions (positive in North America, Africa, and in one case in Europe; and negative in another European case) aligns with our earlier game-theoretic models, suggesting that cyber conflicts often deviate from zero-sum dynamics. This variability underscores the context-dependent nature of cyber operations, where outcomes are highly influenced by specific circumstances, the target’s defensive capabilities, and the broader geopolitical context. It supports our assertion that the strategic landscape in cyberspace is far more complex than traditional conflict paradigms would suggest.
The negative payoff for Venezuela in South America is particularly interesting when viewed through a game-theoretic lens. It demonstrates that even countries with less advanced cyber capabilities can engage in impactful cyber operations, but often at a cost to themselves. This outcome aligns with our findings on the democratisation of cyber warfare, where the relatively low entry barrier allows a wider range of actors to participate. However, it also highlights the potential for miscalculation while planning a cyber strategy, especially for less experienced actors who may not fully anticipate the consequences of their actions.
China’s positive payoff in Asia corroborates our earlier observations about the country’s growing cyber capabilities and strategic acumen in this domain. From a game-theoretic perspective, this suggests that China has successfully identified strategies that maximise its payoff in regional cyber conflicts. This success may be attributed to a sophisticated understanding of the “rules of the game” in cyberspace and an ability to calibrate operations to achieve strategic objectives while minimising potential backlash.
The cases in the Middle East provide a stark contrast and offer valuable insights when analysed using game theory. The negative payoff for the United States, despite its advanced technological capabilities, reinforces our earlier point about the limitations of purely offensive strategies in cyberspace. It suggests that even powerful actors can miscalculate in this domain, potentially overestimating the benefits of aggressive actions or underestimating the target’s resilience and capacity for retaliation. This outcome aligns with our game-theoretic models, which predict diminishing returns for high-impact cyberattacks.
Israel’s case is particularly intriguing from a game-theoretic standpoint. Despite a negative payoff, it is the only instance in our dataset that reaches a Nash Equilibrium. This suggests that Israel has adopted a strategy that, while not optimal in terms of immediate payoff, represents a stable state, given the strategies of other actors in the region. This equilibrium might reflect a long-term approach that prioritises stability and deterrence over short-term gains, aligning with our earlier observations about the evolving nature of cyber deterrence strategies.
The predominant absence of Nash Equilibria across most cases (seven out of eight cases) corroborates our earlier findings about the inherently unstable and dynamic nature of cyber conflicts. In game-theoretic terms, this suggests that most cyber conflicts are in a state of constant flux, with actors continuously adjusting their strategies in response to evolving threats, technologies, and geopolitical circumstances. This instability underscores the challenges in developing sustainable cyber defence strategies and highlights the need for adaptive and flexible approaches to cybersecurity.
When we consider these findings in conjunction with our earlier analysis of attack impact versus attacker payoff, a more comprehensive picture emerges. The prevalence of both positive and negative payoffs across different impact levels reinforces our observation that the relationship between attack severity and strategic benefit is non-linear. This complexity is further evidenced by the regional variations seen in Table 1.
In conclusion, Table 1, when analysed through the lens of game theory and in context with our previous findings, reinforces the notion that cyber conflict is a multifaceted phenomenon that defies simple characterisation. Table 1 highlights the need for nuanced and context-specific strategies in cyberspace, where actors must constantly reassess and adjust their approaches based on a complex interplay of technological capabilities, geopolitical factors, and the anticipated responses of other actors. These insights not only deepen our understanding of the current cyber conflict dynamics but also provide valuable guidance for policymakers and strategists navigating this rapidly evolving domain of international relations.
Conclusions
This study embarked on an ambitious journey to unravel the intricate dynamics of global cyber conflicts through the systematic application of game theory, examining six significant cases spanning North America, South America, Europe, Asia, the Middle East, and Africa. Our research yielded profound insights into the nature of cyber warfare while making substantial contributions to both theoretical understanding and practical applications about cybersecurity. Through an innovative methodological approach combining game-theoretic modelling and comparative case analysis, we uncovered complex patterns and strategic dynamics that characterise state behaviour in cyberspace.
Our methodological framework, combining quantitative game-theoretic modelling and qualitative comparative case analysis, proved particularly effective in capturing both the mathematical precision required for strategic analysis and the contextual richness necessary for understanding complex cyber interactions. This approach enabled us to develop standardised metrics for analysing cyber conflict outcomes while maintaining sensitivity to regional and contextual variations.
The application of game theory to cyber conflict analysis provided several crucial insights that challenge conventional wisdom about international security. Our research demonstrates that traditional assumptions about power relationships and strategic behaviour require significant modification in cyber domain. The game-theoretic models show that states often make decisions under conditions of incomplete information and technological uncertainty, leading to strategic choices that might appear suboptimal under conventional deterrence theory but make sense within the unique constraints and opportunities of cyberspace.
Our comparative analysis across regions displayed both universal patterns and distinct regional variations in cyber conflict dynamics. The study reveals that while certain strategic calculations remain constant across contexts, regional factors, such as technological infrastructure, strategic culture, and geopolitical relationships, significantly influence how states approach cyber warfare. These findings challenge simplistic, one-size-fits-all approaches to cybersecurity and highlight the need for nuanced and context-specific strategies that account for local conditions and capabilities.
The research provides compelling empirical support for the democratisation of cyber warfare, demonstrating how the relatively low entry barriers have enabled a wide range of states to develop significant cyber capabilities. However, our game-theoretic analysis reveals that this democratisation is accompanied by increased strategic complexity and risk, as more actors in the system lead to less predictable outcomes and greater potential for unintended escalation. This is particularly evident in our analysis of medium-sized powers that have successfully leveraged cyber capabilities to achieve strategic objectives traditionally beyond their reach.
A key finding of our study is the preference by states for medium-impact cyber operations, rather than high-impact attacks. This pattern identified through careful game-theoretic modelling, challenges conventional assumptions about escalation dynamics in cyber conflicts and suggests the need for more nuanced approaches to cyber deterrence. Our analysis indicates that states often seek to maintain operations within a “grey zone” which achieves strategic objectives while avoiding escalation to more destructive forms of conflict.
The rapid advancement of AI and other emerging technologies has introduced new dimensions to cybersecurity challenges, as highlighted by recent research (Smith and Johnson, 2024). The integration of AI into cyber warfare is fundamentally altering the speed and complexity of cyber conflicts, while the emergence of quantum computing poses significant challenges to current encryption methods and security protocols (Cummings, 2017, p. 5). Our analysis suggests that these technological developments require substantial adaptation of both theoretical frameworks and practical approaches to cybersecurity.
The expanding IoT and the development of 5G and 6G networks create new vulnerabilities while also offering novel defensive capabilities. As noted by Edwards (n.d.), quantum computing advancements may soon render current encryption methods obsolete, necessitating the development of quantum-resistant security measures. These technological shifts, combined with the growing sophistication of cyber threats, underscore the need for continuous innovation in both offensive and defensive capabilities.
Our study reveals critical implications for the concept of international relations and its practice. The transformation of traditional power dynamics in cyberspace suggests the need to reconceptualise our understanding of state power and influence in the digital age. Small states can achieve significant strategic advantages through well-executed cyber operations, while major powers may find their conventional superiority contested in unexpected ways. This dynamic has profound implications for global security architecture and international stability.
The research also highlights the urgent need for enhanced international cooperation and the development of shared norms in cyberspace. The global nature of cyber threats, combined with the potential for rapid escalation and unintended consequences, as revealed by our analysis, suggests that unilateral approaches to cybersecurity will become increasingly insufficient. The development of international frameworks for managing cyber conflicts becomes crucial for maintaining stability in an increasingly interconnected world.
Looking towards the future, several critical challenges and opportunities emerge from our analysis. The increasing integration of AI and machine learning into cyber operations suggests that the pace and complexity of cyber conflicts will likely accelerate. The potential for autonomous cyber weapons and AI-enabled defence systems raises new questions about human control and decision-making in cyber warfare. These developments require careful consideration of both technical capabilities and ethical implications.
Our research makes several key contributions to the field. Methodologically, it demonstrates the value of combining game-theoretic modelling and comparative case analysis for understanding complex cyber interactions. Theoretically, it advances our understanding of how states behave in cyberspace and why they make certain strategic choices. Practically, it provides insights that can enhance the development of more effective cybersecurity policies and strategies.
The implications of our findings extend beyond the realm of national security, also touching on issues of privacy, civil liberties, and the future of democratic governance in the digital age. As cyber capabilities continue to evolve, societies must grapple with difficult questions about the balance between security and individual rights, the role of technology companies in national defence, and the ethical implications of offensive cyber operations.
Despite the robust findings of this study, several limitations warrant consideration for the sake of future research. The evolving nature of cyber capabilities and the emergence of new technologies, like AI and quantum computing, may alter the strategic calculations that we observed in our historical cases. Additionally, the opacity of cyber operations and the challenge of attribution suggest that our understanding of state strategies and payoffs may be incomplete. Future studies would benefit from access to classified information and real-time data on cyber operations. Furthermore, our game-theoretic approach, although powerful in analysing strategic interactions, may not fully capture the psychological and organisational factors that influence cyber conflict decisions. These limitations point to promising directions for future research, including the development of more sophisticated modelling approaches that can account for emerging technologies, non-rational actors, and complex organisational dynamics in cyber operations.
In conclusion, this study represents a significant advancement in our understanding of global cyber conflict dynamics. Through rigorous methodology and comprehensive analysis of emerging challenges, we developed frameworks that will serve as crucial tools for understanding and responding to future challenges in cybersecurity. As the digital domain continues to transform international relations and security dynamics, the insights provided here will help to guide both scholarly research and policy development in this critical field. The integration of AI, quantum computing, and advanced networking technologies into cyber operations may fundamentally alter the strategic calculus of state actors in cyberspace. Therefore, continuous adaptation of our theoretical frameworks and practical approaches is required to address these emerging challenges in the ever-evolving landscape of global cybersecurity.