Introduction
Counterintelligence refers to activities and measures taken to identify, assess, and counteract the threats posed by foreign intelligence services (FIS) or other malicious actors seeking to gather sensitive information or undermine the security of a country or an organisation. Border security is also the first-level approach against any threats and risks that attempt to enter a state’s security environment (Bellanova and Glouftsios, 2020, pp. 4–6). Both intelligence and security functions utilise processes of data, information and intelligence collection, management, and analysis based on intelligence management models, such as the intelligence cycle and risk analysis models, for instance the European Common Integrated Risk Analysis Model (CIRAM) (Fernández-Rojo, 2021, pp. 14, 22–24; Frontex, 2012a, pp. 5–6).
Travel intelligence TRAVINT also functions as a common intelligence aspect for both travel companies and government security agencies. In this domain, passenger name records (PNR), play a significant role, offering the opportunity to locate any emerging security and intelligence threats (De Hert and Papakonstantinou, 2010, pp. 1–2; US Department of Homeland Security and US Customs and Border Protection, 2013, pp. 1–3).
This paper examines the aspects and components of counterintelligence and border security using a research approach to TRAVINT’s role in both functions. Objectives of the research revolve around investigating the principles and the value of TRAVINT as an intelligence input for both counterintelligence and border security functions. The research methodology used in this study is a multifaceted approach that integrates empirical analysis, thorough examinations of academic papers, and the invaluable inclusion of expert insights gleaned from a meticulous examination of public documents from both the United States and the European Union (EU). This comprehensive methodology is designed to provide a holistic and well-rounded perspective on counterintelligence, border security, and the emerging field of TRAVINT. It is worth noting that the term “TRAVINT” does not seem to have been documented previously in any existing academic article or book. Instead, it emerges as a novel concept closely linked to the official documents released by the European Commission and Frontex, both of which are extensively referenced and cited in this study. This observation underscores the innovative and timely nature of the research, as it seeks to elucidate a concept that has not yet been widely explored in academic or literary sources. Later in the paper, the author strives to address a notable research gap by examining the underexplored intersection of TRAVINT with other intelligence and security sectors. These examinations endeavour to highlight the worthiness of TRAVINT as an emerging intelligence sector.
While the paper offers valuable insights into the emerging field of TRAVINT, it is important to acknowledge its limitations, one of which is its predominantly US- and EU-centric focus. The research heavily relies on data and academic papers from the United States and EU, which may inadvertently skew the findings and recommendations towards the specific dynamics of these regions. TRAVINT raises a global concern, and its implications are not limited to these areas alone. Consequently, the applicability of the research's insights in the regions such as Asia, Africa, or South America may require further exploration and adaptation. Furthermore, the paper’s exclusive focus on public and academic sources might overlook valuable insights from non-traditional and on-the-ground intelligence sources. Therefore, to enhance the comprehensive applicability of TRAVINT, the future research should try to broaden its geographical scope and incorporate diverse perspectives and sources.
Counterintelligence Theory and Practice
Counterintelligence theory refers to the principles, concepts, and strategies used in the field of interfering malicious intelligence acts (Ehrman, 2009, pp. 4–5, 14–18; Prunckun, 2019, pp. 37–51). It is a discipline within intelligence and security that focuses on identifying, understanding, and countering threats posed by FIS, such as espionage, and covert activities. It involves efforts to protect a country’s national security secrets and prevent the unauthorised acquisition of sensitive information (Melendez, 2019, pp. 1–4). Theoretically, it is a subject of interest for both former intelligence officials and security studies, strategic studies, and intelligence studies. In particular, relevant literature arising from former intelligence executives of western countries’ agencies such the Central Intelligence Agency (CIA), Federal Bureau of Investigation (FBI), MI6, and MI5. The written efforts of John Ehrman, and Michelle K. Van Cleave set up the strategic and operational aspects of the matter but often lack an academic and structured approach (Cram, 1993, pp. 1–80; Ehrman, 2009, pp. 1–27; Van Cleave, 2007, pp. 1–44). Another publication that covers a wider range of counterintelligence is Johnson’s (2010) handbook which approaches the subject comprehensively, focusing on historical aspects and emphasising its ever-increasing value. In the same direction, Sims and Gerber’s (2009, pp. 34–36, 128–129) book, Vaults, mirrors, and masks: Rediscovering U.S. counterintelligence, offers a focus on decision-making and the denial deception features of the process.
Counterintelligence, much like the metaphorical “sword” and “shield” used in the Soviet parlance to refer the KGB (Komitet gosudarstvennoy bezopasnosti), consists of two distinct yet interconnected functions, the offensive and defensive functions (Prunckun, 2019, pp. 25–28; Richelson, 1986, pp. 1–10). The offensive function is equated to the “sword,” as it involves proactive efforts to identify, infiltrate, and disrupt intelligence activities which may encompass espionage, cyber attacks, or covert operations (Prunckun, 2019, pp. 49–52). This proactive stance is focused on identifying adversaries, collecting intelligence on their intentions, and neutralising their efforts. The main component of offensive counterintelligence is counterespionage (Prunckun, 2019, pp. 55, 216–217). It is a multifaceted discipline composed of detection, deception, and neutralisation. Firstly, it involves the meticulous detection of espionage activities and covert intelligence threats directed against an organisation or nation (Melendez, 2019, pp. 14–17). This process entails constant monitoring and vigilance to identify potential spies and their tactics. Secondly, it utilises deception techniques to confound adversaries, misdirect their efforts, and protect sensitive information (Prunckun, 2019, p. 9). These tactics may involve creating false leads, disinformation campaigns, or covert operations to disrupt the plans of intelligence adversaries (Prunckun, 2019, pp. 9, 49). Finally, once detected, counterespionage focuses on the neutralisation of espionage threats, ensuring that the nation’s secrets remain safe (Prunckun, 2019, pp. 49–50).
In contrast, the defensive function operates as the “shield,” forming a protective barrier to prevent and mitigate espionage, sabotage, and other intelligence threats targeted at an organisation or nation (Melendez, 2019, pp. 20–23). This defensive aspect is the guardian of an entity’s secrets, ensuring that sensitive information is protected, and critical assets remain secure (Prunckun, 2019, pp. 55–64).
Specifically, threat identification, a fundamental element of defensive counterintelligence, involves the systematic analysis and assessment of potential threats—whether they emanate from FIS, insider threats, or other sources (Melendez, 2019, pp. 12–14; Prunckun, 2019, pp. 65–74). It is a process that aims to recognise the vulnerabilities and risks (Prunckun, 2019, pp. 75–78). Information protection is also another pivotal aspect of defensive counterintelligence. It encompasses the secure handling of sensitive data, ensuring it remains inaccessible to unauthorised parties (Prunckun, 2019, pp. 55–64; Sims and Gerber, 2005, pp. 226–228). Over time, the responsibility for overseeing the procedures and operations associated with counterintelligence is entrusted to the collaborative efforts of proficient intelligence officers specialising in border and national security. Success of counterintelligence depends on the collection of appropriate information, which will lead, through the use of analytical tools, to the identification of any security gap and threat (Melendez, 2019, pp. 17–19).
Border security
Border security theory refers to the concepts and strategies used to protect a country’s borders and ensure the security of its territory (Frontex, 2012b, p. 12; Oliveira Martins et al., 2022, pp. 1–3; Wagner, 2021, pp. 77–81). It encompasses various approaches and practices, including the deployment of physical barriers, surveillance technologies, law enforcement personnel, and immigration policies (Frontex, 2012a, pp. 5–6). The main objective of border security is to prevent unauthorized entry, detect and intercept illegal activities, such as smuggling and terrorism, and maintain the safety of a nation (Frontex, 2012a, pp. 27–30; Hansen and Pettersson, 2021, pp. 3, 10; Oliveira Martins et al., 2022, pp. 8–11).
Border security management relies on risk analysis models in support of effective border surveillance and control (Frontex, 2012a, pp. 10–12; Jeandesboz, 2020, pp. 15–16; Wagner, 2021, p. 234). Risk analysis is a process used by border security agencies to assess potential threats and vulnerabilities at the border and prioritise their response accordingly (Shepherd, 2022, pp. 6–9). In the last decade, agencies such as Frontex in Europe and Customs and Border Protection (CBP) in the United States have developed their own risk analysis models such as CIRAM, including specific intelligence procedures in their daily functioning (Frontex, 2012a, pp. 36–37; Léonard, 2010, pp. 1–5; Liashuk and Tsaruk, 2021, pp. 2–4).
Specifically, procedures of risk analysis are employed to assess risks and identify potential threats (Frontex, 2012a, pp. 20–26; Wagner, 2021, pp. 337–339). Their data collection processes may encompass border and internal security relevant data and information, such as traveller data (e.g. PNR information), cargo manifests, intelligence reports, watchlists, and other sources of data, to develop a comprehensive understanding of potential threats from terrorism, smuggling, illegal immigration, and more (Morral et al., 2011, pp. 23–24). The data mining and analysis of these sources of information lead to pattern recognition and predictive modelling that assist in modus operandi and identificationof relationships that may indicate potential security risks (Frontex, 2013, pp. 13–23; Liashuk and Tsaruk, 2021, pp. 4–6).
Furthermore, border and security agencies proceed to risk prioritisation by allocating their resources, focusing on the highest-risk areas or individuals, and promoting strategies to mitigate the most serious problems, such as dealing with serious organised crime and terrorism (Frontex, 2013, p. 33–35; Wagner, 2021, pp. 349–350). This allows them to optimise security measures and respond to potential threats more effectively by deploying advanced screening technologies or targeting specific routes or individuals for further inspections (Jeandesboz, 2020, pp. 15–16; Oliveira Martins et al., 2022, pp. 4–5; US Department of Homeland Security Privacy Office, 2017, pp. 25–27; Wagner, 2021, pp. 319–321).
By combining border security intelligence and risk analysis, authorities can eventually -proactively identify and address potential security threats while efficiently managing the flow of legitimate travellers and goods across borders (European Parliament, 2016, pp. 14–15).
Defining Travel Intelligence and Counterintelligence
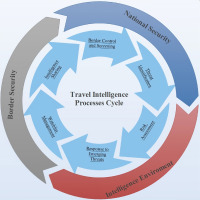
TRAVINT plays a decisive role in ensuring national security and proper border security by providing valuable information about potential threats, risks, and suspicious activities related to those people and material that are, geographically, in transition. It involves the systematic collection, analysis, and utilisation of travel-related information and intelligence to enhance security measures and law enforcement efforts. It focuses on data generated by activities such as passenger travel, including PNR, advance passenger information (API), and the European Travel Information and Authorisation System (ETIAS) (European Parliament, 2016, pp. 30–33; Frizberg, 2023, pp. 1–4; Namazov, 2022, pp. 7–11; National Counterterrorism Center, 2013, p. 60; Priestley and Beauvais, 2021, pp. 3–6; Romanian Parliament, 2019, p. 1; Wagner, 2021, p. 362).
The history of TRAVINT in the context of the EU and the United States has evolved over the years in response to the growing need for enhanced security measures. In the EU, the Europol Travel Intelligence Center (ETIC) was established in 2019 as part of Europol’s horizontal operational services. It represents a coordinated effort to use travel-related data to combat security threats within the EU (Frontex, 2020, pp. 1–10; Romanian Parliament, 2019, p. 1). The development of such capabilities is in line with the EU’s commitment to the collection and sharing of travel data as outlined in the EU PNR directive 2016/681 (Priestley and Beauvais, 2022, p. 9). In the United States, similar efforts have been made through organisations, such as the transportation security administration (TSA) and the Department of Homeland Security (DHS), by gathering travel-related data for security and border protection purposes. Both regions have recognised the significance of TRAVINT in bolstering their security and law-enforcement efforts, making it a pivotal component of their national and regional security strategies.
Furthermore, intelligence products emerging from TRAVINT provide critical insights into traveller movements, patterns, and potential security threats (Frontex, 2020, pp. 1–10). These products are mainly utilised for the following activities:
Threat identification: TRAVINT helps to identify individuals or groups who may pose a threat to national security. By monitoring travel patterns, conducting background checks and analysing passenger data (such as PNR information), authorities can identify individuals who have connections to terrorism, criminal activities, or other security concerns (National Counterterrorism Center, 2013, p. 6; US Department of Homeland Security Privacy Office, 2015, pp. 14–16, 2017, pp. 2–4).
Risk assessment: TRAVINT provides insights for assessing the potential risks associated with certain destinations, travel routes, or transportation modes. This information helps authorities to determine the level of security measures required and allocate resources accordingly (National Counterterrorism Center, 2013, p. 5; US Department of Homeland Security Privacy Office, 2015, pp. 15–16; US Government Publishing Office, 2011, pp. 4–14).
Response to emerging threats: TRAVINT enables authorities to respond promptly to emerging threats or security incidents. By continuously monitoring and analysing travel-related information, agencies can detect potential trends, patterns, or changes in threat levels and adjust their security strategies accordingly (National Counterterrorism Center, 2013, p. 35; US Department of Homeland Security Privacy Office, 2015, p. 11).
Watchlist management: TRAVINT is used to maintain and update watchlists, which include individuals who are security risks. These watchlists help border security agencies to identify and screen individuals who should receive extra focus during travel (National Counterterrorism Center, 2013, pp. 6–10; US Department of Homeland Security Privacy Office, 2015, p. 13, 2017, p. 8).
Intelligence-sharing: Collaboration and sharing of TRAVINT among different national security agencies and international partners is crucial. By sharing relevant information, such as suspect profiles, travel itineraries, or suspicious activities, countries can enhance their collective ability to detect and prevent security threats (Frontex, 2020, pp. 1–10; US Department of Homeland Security Privacy Office, 2015, pp. 15–20, 2017, pp. 14–15).
Border control and screening: TRAVINT supports the implementation of effective border control measures. By analysing travel data and intelligence, authorities can identify high-risk travellers and allocate resources towards those who require further scrutiny and monitoring (National Counterterrorism Center, 2013, pp. 43–46).
With regard to PNR, it is a specific record that contains information about a passenger’s travel arrangements (De Hert and Papakonstantinou, 2010, pp. 1–4; European Union, 2016, pp. 1–4; Glouftsios and Leese, 2022, pp. 1–2; Namazov, 2022, pp. 10–12). It typically includes details such as the passenger’s name, contact information, travel itinerary, ticket information, seat assignments, and other relevant data (Glouftsios and Leese, 2022, pp. 3–5; US Department of Homeland Security and US Customs and Border Protection, 2013, pp. 1–8). PNR data is collected by airlines and travel agencies as part of the booking process and can provide valuable information to intelligence and law enforcement agencies for various purposes, such as identifying potential threats, tracking individuals of interest, or identifying patterns of suspicious travel behaviour (US Department of Homeland Security Privacy Office, 2015, p. 13). It’s important to note that the collection and use of PNR data for intelligence purposes may have privacy implications and it is subject to legal and regulatory frameworks in different jurisdictions (De Hert and Papakonstantinou, 2010, pp. 1–4). Nonetheless, it is a critical part of the detection function within the domain of both defensive and offensive counterintelligence (Prunckun, 2019, pp. 121, 147, 178, 185). TRAVINT, in the context of PNR, also refers to the analysis and use of PNR data for intelligence and security purposes (De Hert and Papakonstantinou, 2010, pp. 1–4; European Union, 2016, pp. 1–4; Glouftsios and Leese, 2022, pp. 6–7). By analysing PNR data, intelligence agencies can detect anomalies or red flags that might indicate suspicious or illicit activity, such as individuals travelling to high-risk destinations, multiple individuals booking tickets on the same itinerary with no apparent connection, or other patterns that may warrant further investigation (Namazov, 2022, pp. 7–12). Overall, TRAVINT derived from PNR data can help enhance security, prevent terrorism, combat human trafficking, and support law enforcement efforts (Rudner, 2014). It can be used as part of a larger intelligence picture to assess and mitigate potential risks associated with travel (Barnea, 2019, pp. 9–10). That said, it does require considerable dedication to cooperation between all relevant defence and security agencies, as well as the commercial sector, to provide access to the data/information/intelligence for all.
In the context of border security, PNR has an important role in supporting the screening and vetting processes carried out by the authorities (European Union, 2016, pp. 1–4; Glouftsios and Leese, 2022, pp. 7–9; Namazov, 2022, p. 26; Van Dongen, 2010, p. 5). Border security agencies use PNR data to identify potential security risks and to facilitate the efficient and effective management of border control. By analysing PNR data, border security officers can determine whether any passengers on incoming or outgoing flights raise concerns or require additional scrutiny. Plus, PNR data allows border security agencies to identify individuals who may be on watchlists, such as terrorist watchlists or those involved in criminal activities (European Union, 2016, pp. 8–11; Glouftsios and Leese, 2022, pp. 12–15; Rudner, 2014; US Department of Homeland Security Privacy Office, 2017, p. 18). It can also assist with the identification of passengers with suspicious travel patterns, such as multiple one-way tickets or frequent travel to high-risk destinations.
Travel Intelligence, Border Security, and Counterintelligence
Counterintelligence and border security are two separate concepts, but they intersect and are mutually reinforcing within the context of national security. As counterintelligence refers to activities undertaken by a government or an organisation to identify, understand, and counter threats posed by FIS or other threat actors, it involves gathering information, analysing intelligence, and implementing measures to protect sensitive information and thwart espionage or sabotage attempts (Melendez, 2019, pp. 12–14; Riehle, 2015). Concurrently, border security focuses on protecting a country’s borders and ensuring the integrity of its territory. It involves measures such as physical barriers, surveillance systems, patrols, and presence of law enforcement to prevent unauthorised entry, smuggling, trafficking, and other illegal activities (Oliveira Martins et al., 2022, pp. 10–14). Several of these security measures are described by Prunckun (2019) within the context of defensive counterintelligence and typically as part of the defence counterintelligence tenet elaborating on defence-in-depth.
While counterintelligence primarily focuses on intelligence gathering and protection on a country’s own territory, it can intersect with border security when there is concern about FIS or threat actors attempting to exploit vulnerabilities at the border. In such cases, counterintelligence efforts may be integrated into border security strategies to identify and mitigate potential threats. Eventually, both counterintelligence and border security play important roles in maintaining national security, but they deal with different aspects of protecting a country’s interests.
In the context of PNR, counterintelligence may involve the analysis of PNR data to -identify suspicious travel patterns or activities that could indicate espionage, sabotage, or other threat activities conducted by FIS or individuals acting on their behalf. Certainly, detecting espionage and intelligence threats from PNR data can be a complex task that requires careful analysis and investigation. PNR data is primarily used by authorities for purposes, such as preventing terrorism and serious organised crime (Frontex, 2020, pp. 1–10). However, by analysing PNR data, intelligence agencies can potentially research for indicators, such as multiple individuals travelling together with no apparent connection, sudden changes in travel plans, unusual or high-risk destinations, or other suspicious patterns, that may suggest intelligence-related activities. Specifically, the tactical and operational approaches for detecting this pursuit are as follows:
Pattern intelligence analysis: Analysing patterns in PNR data can help identify anomalies or suspicious activities. This can include looking for unusual travel itineraries and frequent changes in travel plans or connections to known espionage hotspots (European Commission, 2023; Frontex, 2020, pp. 1–10).
Social network analysis: Conducting link analysis on PNR data can help identify connections between individuals or groups that may be involved in espionage activities. This can involve analysing shared travel patterns, common contacts, or other indicators of collaboration (Shulsky and Schmitt, 2009, pp. 11–18).
Travel behavioural analysis: Examining the behaviour of individuals or groups in PNR data can provide insights into potential espionage activities. This can include analysing social behavioural and travel patterns, unusual booking behaviour, or other indicators of suspicious activity (European Commission, 2023; Frontex, 2020, pp. 1–10).
Integration with other intelligence sources: Integrating PNR data with other intelligence sources, such as open-source intelligence or human intelligence (HUMINT), can provide a more comprehensive picture of potential espionage activities. This can help corroborate findings and provide additional context (European Commission, 2023; Frontex, 2020, pp. 1–10).
Considering the HUMINT sources, offensive counterintelligence efforts may involve monitoring and assessing the activities of FIS or suspected foreign agents who may be attempting to collect information or exploit vulnerabilities within a country or organisation (Stouder and Gallagher 2013, pp. 3–12). This may include tracking their travel patterns, understanding their contacts and associations, and identifying potential threats or vulnerabilities. On these occasions, watch-listing operational processes are promoted (National Counterterrorism Center, 2013, pp. 11–12; US Department of Homeland Security Privacy Office, 2017, p. 27; US Department of Homeland Security and US Customs and Border Protection, 2013, pp. 1–8).
The case of Alexander Yuk Ching Ma
The case of Alexander Yuk Ching Ma involves a former CIA officer who was arrested and charged on 14 August 2020 with espionage-related offences (Office of Public Affairs, 2022, pp. 1–5). Alexander Yuk Ching Ma was a naturalised US citizen born in Hong Kong, who worked as a CIA officer in the 1980s and later as a contract translator for FBI in the 2000s and was charged with conspiracy to communicate, deliver, and transmit national defence information to the Chinese government for more than a decade. He allegedly provided information about CIA’s personnel and tradecraft to Chinese Intelligence for personal gain (US Department of Justice, 2020).
Specifically, the case against him has been described as complex and there have been requests for a competency evaluation to determine his ability to stand trial. According to court documents, Ma expressed his desire for the “motherland” to succeed during conversations with an undercover FBI agent posing as a Chinese intelligence officer. Eventually, senior officials referred to Ma as a classic example of an insider threat. Their comments highlight the issue of former American intelligence officers who have betrayed their colleagues, country, and democratic values to support an authoritarian regime (US Department of Justice, 2020, pp. 15–19). It is important to note that Ma’s wife travelled to Shanghai to deliver a laptop to Chinese intelligence, and Ma used to travel frequently to Hong Kong and China. Other open-source intelligence (OSINT) articles mentioned that he was “accused of stealing classified information and giving it to China in exchange for money, travel reimbursements and a set of golf clubs” (Boylan, 2023).
Furthermore, in addition to the official public statements and information concerning the examined case, it becomes evident that these sources are, in part, predicated upon the use of travel intelligence. This intelligence arises from the collation of data and information pertaining to Ma’s travel patterns and operational methods (US Department of Justice, 2020, p. 15–19). His journeys to Asia, the intricacies of his travel arrangements, and the payment methods employed have plausibly contributed to the understanding of his associations with Chinese intelligence officers. It was also conceivable that his apprehension was linked to the implementation of specific watch-listing techniques as delineated in the documentation of American intelligence agencies, exemplifying a counterintelligence--oriented approach (US Department of Justice, 2020, pp. 15–19).
TRAVINT watch listing is a process where certain individuals are placed on watchlists to enhance security measures and prevent potential threats to national security. Subsequently, types of individuals or circumstances that might lead to watch listing may be as follows:
Known or suspected terrorists: Individuals who have been identified as being involved in or having ties with terrorist organisations might be placed on TRAVINT watchlists to prevent them from travelling freely.
High-risk individuals: Individuals who are deemed to pose a potential security risk, such as those with a history of violence or criminal activity, may be watch-listed to ensure enhanced scrutiny is given to their travel patterns.
Suspected or known spies: Individuals suspected or known to be involved in espionage activities may be placed on travel watchlists to monitor their movements and prevent unauthorised access to sensitive locations or classified information.
Conclusion
In conclusion, counterintelligence theory is a dynamically evolving field that adapts to emerging threats, technological advancements, and shifts in geopolitical landscape (Prunckun, 2019). The evolving theories and practices within counterintelligence continually respond to new challenges and vulnerabilities. Given the increasingly complex intelligence and security environment, there is a growing imperative for functional interconnections between various security processes, such as border security.
This paper has approached the security and intelligence functions of counterintelligence and border security by examining and discussing their shared aspects, with a particular focus on TRAVINT. The paper has also highlighted the increasing demand for and importance of TRAVINT, emphasising its processes and tactical and operational co-approaches in conjunction with counterintelligence and border security.
From this perspective, TRAVINT emerges as an invaluable source of information, providing the legal, intelligence, and security enforcement sectors with necessary intelligence inputs to address national threats and risks. It is essential to highlight that the utilisation of PNR data should always occur in strict compliance with state legislation and with full respect for relevant human rights. Furthermore, it is evident that further academic and operational research is required to delve into the specific use of information and intelligence related to TRAVINT, with the aim of establishing a new sector within academic intelligence research.
Last but not least, the paper presents a visionary perspective on the future applications of TRAVINT, highlighting its crucial role in safeguarding global security. In an increasingly interconnected world, countries serving as international travel hubs, such as the Emirates (Dubai), the Netherlands (Amsterdam), Germany (Munich), the United Kingdom (London), and key African cities such as South Africa’s Johannesburg and Cape Town, face burgeoning challenges in terms of counterintelligence and border security. As these pivotal transit points continue to attract an influx of travellers, the need for advanced intelligence operations to thwart potential threats has become paramount. The insights derived from this research have the potential to reshape international travel security strategies, making these global transit hubs safer, and reinforcing the broader global security ecosystem.