Introduction
The goal of this study is to detect and prevent harmful attacks and operations in society’s information environment, and to secure, protect, defend and maintain society’s vital functions, activities and information (The Security and Defence Committee, 2006). The components of defence strategies vary according to whether attacks are physical or whether they are operations against state dependency. Society must be defended against false or incorrect information that can cause harm. Society needs to defend itself against cyber operations and cyber attacks, the goals of which are to damage society’s critical infrastructure or critical information. Counter-defence strategies are also needed in society’s information environment to recognise and identify operations and attacks at different levels, that is, at the state, society, organisational, company, technical, legislative, security, individual, and international levels. Information confidentiality, integrity and availability must be protected at all these levels.
In this study, information environment (IE) is defined as “Information, aggregate of individuals, organisations and systems that receive, collect, process and convey/disseminate the information, or act on information, and the cognitive, virtual and physical space in which this occurs” (NATO, 2012 p. 3, Armistead and United States and Joint Forces Staff College, 2004 pp. 13–20), and includes both military and non-military information operations (IO) and information warfare (IW) (The Security and Defence Committee, 2006).
The focus of this study is on society’s IEs, and a society is defined as “a group of individuals involved in persistent social interaction, or a large social group sharing the same geographical or social territory, typically subject to the same political authority and dominant cultural expectations” (Society, 2020).
Although previous studies (Lehto et al., 2017, Nimmo, 2015, Pomerantsev, 2015, Sigholm, 2013, p. 51, Mäntylä, 2014, Joint Chiefs of Staff, 2013, Armistead et al., 2004 pp. 13–20, Schechtman, 1996) have shown that a great deal of components of defence strategies exist in societies’ IE, qualitative research of the origins of components of defence strategies and how a society becomes aware of these is lacking. In order to obtain a clear understanding of their influence, components of defence strategies must be examined in a real society. Such an investigation would improve the ability to understand the possible new approaches of future components of defence strategies. This study tackles these issues.
Past studies and empirical evidence were applied in this qualitative in-depth case study (Benbasat et al., 1987, Yin, 2003), which identifies the components of defence strategies in a society’s IE. The data collected was analysed using the Grounded Theory (GT) approach, and a conceptual framework was developed with components of defence strategies and the relationships between them (Glaser and Strauss, 1967). The goal of this study was to explore the components of defence strategies of a society’s IE, the extent to which these components of defence strategies are shaped by the IE context, and how these components of defence strategies are inter-related.
The study made 146 components of defence strategy observations supported by empirical evidence, and these observations were categorised using GT analysis (Glaser and Strauss, 1967). The analysis revealed 16 components of defence strategies as follows: Total Defence, Operative Capability, Cyber Defence, Defence against Cyber Space Operations, Critical Infrastructure Protection (CIP), Cyber Capability, Observation-Orientation-Decision-Action (OODA) Defence, Espionage, Cyber Intelligence, Counter Intelligence, Information Security and Defence, Information Security Breach Investigation, Recognition Primed Decision Model of Rapid Decision Making (RPD Model), Defence with Law, Non-Physical Network Defence, and Strategic Communications (StratCom). These components of defence strategies were inter-related, and 9 higher levels of abstraction of statements based on the conceptual framework, propositions for components of defence strategies, and their relationships between the components of defence strategies were found.
The rest of the paper is organised as follows: section two discusses the related research, section three deals with the research method, section four outlines data collection and categorisation, and section five shows the data analysis. Finally, section six contains the conclusions.
Related research
Defence includes various components of strategies, such as Total Defence, which means protecting a state’s independence and its citizens, trying to estimate an adversary’s potential capabilities, and protecting society’s vital functions from threats or actual attacks (Lehto, 2016, Ministry of Defence, 2006, p. 23). Lehto (2016) claims that an important part of total defence is military Cyber Defence, which is the combined capability of intelligence, influence and protection (Lehto et al., 2017). Furthermore, network surveillance is a part of cyber defence and it means defence to protect, monitor, analyse, detect and respond to network attacks, intrusions, disruptions, or any unauthorised actions that would destroy information systems and the networks connected to them through computer networks (Lehto, 2015, p. 18; Ottis, 2013). According to Hausken (2019, p. 364 and Wei et al., 2015) networks including electrical power, communication, computers, command and control, production or multiple military army networks can be under attack.
According to Yaghlane and Azaiez (2016), Wei et al. (2015), Sigholm (2013, p. 51), Lehto (2015), defence against Cyber Space Operations provides strategic benefits in cyberspace. Lehto et al. (2017, p. 33) in turn explain Cyber Capability as raising the attack threshold, efficient observation ability, situation awareness, decision-making, and management processes suitable for the cyber world.
One of the capabilities of a defence system, or part of it, is Operative Capability (Ministry of Defence, 2006). The performance of a defence system, or part of it, is affected by its skills set, material and operating principle. Operative Capability consists of effectiveness, life cycle and usability (Ministry of Defence, 2006). According to Lehto (2014, p. 54), capability is the ability to achieve the desired effectiveness and take into account threats, operating environment and other circumstances.
Critical infrastructure includes both physical structures and buildings, and digital activities and services: energy production, distribution and transfer systems, traffic and logistics, information and communication systems, and water and waste disposal. Critical Infrastructure Protection (CIP) means the protection of critical infrastructure (Mäntylä, 2014). Dunn (2005, p. 266) claims that “the objects of protection are services and their role and function for society”. Geers (2011, p. 135) claims that much critical infrastructure is in private hands, outside of government protection and oversight. According to Hausken (2019, p. 364) and Quijano et. al. (2016), societal infrastructures that each consist of various sectors which interact can be under attack.
The Secretariat of the Security Committee (2018, pp. 16–17) states that Information Security Breach Investigation, which is a cyber operation and an organised way of managing the aftermath of a security breach or cyber attack (IT incident or computer incident or security incident), can include incident response actions such as protecting evidence, digital forensics, malware analysis, log analysis and general investigations of the security breach’s influence or scope, in order to limit the damage.
Von Clausewitz (1832) points out that Espionage is the same as Intelligence, and adversaries and their country must be investigated before the country’s plans and operations.
The Secretariat of the Security Committee (2018, p. 23) and Clark (2013) define Cyber Intelligence as both communications and telecommunications intelligence and information system intelligence inside or outside the homeland state, which is state-authorised. Wihersaari (2015, p. 6), on the other hand, points out the difference between cyber security and cyber offensive from two perspectives, that is, the role and manifestation of intelligence. In the former, cyber security is perceived “from a threat awareness and vulnerability management perspective, whereas in the latter, cyber intelligence is treated as an enabling and target designating element.” Geers (2011, p. 100) states that attackers should be forced to lose time, wander into digital traps, and betray information regarding their identity and intentions. According to the Secretariat of the Security Committee (2018, p. 26), cyber spying is part of cyber intelligence. The spying of networks, their devices and software, is targeted at states, citizens or any organisation or company using targeted malware attacks. Spyware is a malware program that collects data from the information system executing the spyware. It can also be called as a digital spy (Geers, 2011). The data can be IP and Domain Name System (DNS) information, credit card information, bank account ID, passwords, browser history or the content of documents (Mäntylä, 2014 p. 14).
Joint Publication 1–02 (2010, p. 53) states that in Counter Intelligence (CI), information is gathered and defence activities are conducted against hostile actors for several purposes, “such as to identify, deceive, exploit, disrupt, or protect against espionage, other intelligence activities, sabotage, or assassinations conducted.”
Cline (1993, p. 147) and NATO StratCom COE (2016) state that the Recognition Primed Decision (RPD) Model of Rapid Decision Making helps experienced decision-makers apply their past experience to make the right decisions the first time round, thus eliminating the need to make other decisions.
Nimmo (2015) and Pomerantsev (2015) state that Information Security and Defence means protecting credible sources of information. Raggad (2010) and Mäntylä (2014) claim that confidentiality means protecting information from unauthorised access or disclosure, integrity means protecting information from unauthorised modification, and availability means that information security is achieved when users receive the required information from the appropriate resource. Information Security and Defence means several arrangements, such as access control; locking premises; safety preservations and disposal of documents; data encryption and backups; fire-walls; antivirus programs and certificates; securing documents, hardware and software; data communications; and operational security (Secretariat of the Security Committee, 2018, p. 15; Hausken, 2019, p. 364). NATO StratCom COE (2016, p. 8) states that “hostile actors try to affect decision making by distorting the quality of information, controlling access to information or influencing people’s perception and understanding of the information they are in contact with”. Dunn (2005, p. 261), the Secretariat of the Security Committee (2018, p. 14) and Mäntylä (2014) claim that information, data and software of computer systems that operate critical infrastructure must be protected. In relation to this, Dunn (2005, p. 261) mentions that “information is an issue of national security, because the society is dependent on ICT. Therefore, information defence must happen on technical, legislative, organisational, or international levels.”
Jackson (2015, p. 6) argues that Defence with Law means arrangements against the incorrect usage of legitimate systems and ways of doing things right – both internationally and domestically – in order to obtain political superiority or commercial benefits.
The Ministry of Defence (2016), Lehto (2015), Sillanpää et al. (2015), the Joint Chiefs of Staff (2013) and Schechtman (1996) claim that the Observation-Orientation-Decision-Action (OODA) loop, which is a cybernetic twin loop model of human decision-making in defence, means protecting the IE by defending it against IO and cyber operations or defending oneself against network warfare. Network warfare is quite close to cyber warfare. Cyber warfare includes cyber penetration, cyber manipulation and cyber robbery (Sigholm, 2013, p. 51, Lehto et al., 2017).
Conley et al. (2016) state that Non-physical Network Defence is defence against security, business, intelligence, political, contact and company networks that are guided, owned and funded by a foreign state, as well as opaque foreign state networks.
Strategic Communications (StratCom ) means defence against IO by which different information influences are controlled in a military crisis (Hollis, 2011), public diplomacy (PD), public affairs (PA), military public affairs (MPA), and psychological operations (PSYOPS) (NATO StratCom COE, 2015, U.S. Department of Defence, 2008). In Strat-Com, IO and public relations influence are carried out and are targeted at domestic and foreign media and audiences (Luoma-aho, 2015). StratCom is connected to IW and network control and management (Jantunen, 2013). Table 1 shows the synthesis of the past studies concerning components of defence strategies.
Table 1
The synthesis of the past studies
| Thematic category | Literature Source |
|---|---|
| Total Defence | Hausken, 2019, p. 364; Lehto, 2016;Ministry of Defence, 2006, p. 23 |
| Operative Capability | Lehto, 2014, p. 54; Ministry of Defence, 2006 |
| Cyber Defence | Hausken, 2019, 364; Lehto et al., 2017;Lehto, 2016; Lehto, 2015, p. 18;Wei et al., 2015; Ottis, 2013 |
| Defence against Cyber Space Operations | Yaghlane and Azaiez, 2016; Wei et al., 2015; Lehto, 2015; Sigholm, 2013, p. 51 |
| Critical Infrastructure Protection | Hausken, 2019, p. 364; Quijano et. al., 2016; Mäntylä, 2014; Geers, 2011, p.135; Dunn, 2005, p. 266 |
| Cyber Capability | Lehto et al., 2017, p. 33 |
| OODA Defence | Lehto et al., 2017; The Ministry of De- fence, 2016; Lehto, 2015; Sillanpää et al., 2015; The Joint Chiefs of Staff, 2013; Sigholm, 2013, p. 51; Schechtman, 1996 |
| Espionage | Von Clausewitz 1832 |
| Cyber Intelligence | Secretariat of the Security Committee, 2018, p. 23, p. 26; Wihersaari, 2015, p. 6; Mäntylä, 2014, p.14; Clark, 2013;Geers, 2011, p. 100 |
| Counter Intelligence | Joint Publication 1–02, 2010, p. 53 |
| Information Security and Defence | Hausken, 2019, p. 364; Secretariat of the Security Committee, 2018, pp. 14–15; NATO StratCom COE, 2016, p. 8; Nim- mo, 2015; Pomerantsev, 2015; Mäntylä, 2014; Raggad, 2010; Dunn, 2005, p. 261 |
| Information Security Breach Investigation | Secretariat of the Security Committee, 2018, pp. 16–17 |
| RPD Model | NATO StratCom COE, 2016;Cline, 1993, p. 147 |
| Defence with Law | Jackson, 2015, p. 6 |
| Non-Physical Network Defence | Conley et al., 2016 |
| Strategic Communications | NATO StratCom COE, 2015; Luoma- aho, 2015; Jantunen, 2013; Hollis, 2011; U.S. Department of Defence, 2008 |
Thus, despite numerous excellent past studies on components of defence strategies, the literature has neglected the relationships of these components of strategies with each other. Therefore, this study responds to the need for further research, and offers both practical and theoretical knowledge on components of defence strategies in a society’s IE, exploring their relationships with each other.
The profound analysis of past components of defence strategy research thus led to the formulation of two research questions (RQs): 1) What are the components of defence strategies in a society’s IE?; and 2) How are the components of defence strategies in a society’s IE related to each other?
Research method
The GT approach follows different phases of data analysis and uses content analysis as part of its categorisation method as follows: 1. Identification of thematic categories in the empirical data using content analysis. 2. Definition of the thematic category based on the empirical data. 3. Search for appropriate literature to be used as evidence for the identified thematic category. 4. Search for similar thematic categories in the empirical evidence to enable mutual exclusion (it is not wise to use thematic categories that use the same definition but are labelled (titled) differently). 5. Search for relationships between the thematic categories. 6. Determination of higher level of abstraction of statements about the relationships between the thematic categories, and propositions for the categories. The statements are based on empirical evidence. 7. Creation of a conceptual framework of thematic categories and their relationships in order to visualise results. The final product resulting from creating a theory from the case studies may be a concept, a conceptual framework or propositions, or possible mid-range theory (Eisenhardt, 1989, Mustonen-Ollila and Heikkonen, 2009).
According to Markus and Robey (1988), theories are established using a variance or process theory. Process theory tries to understand the phenomena in the terms of the cause-effect events leading to an outcome. Variance theory explains phenomena in terms of the relationships that link hypotheses between the dependent and independent variables. The emergent theory, which can be a conceptual framework, the various concepts, and the concept categories and their relationships with and dependencies on each other offer a new type of theoretical construct for understanding the studied phenomena from different perspectives (Mustonen-Ollila and Heikkonen, 2009). According to Eisenhardt (1989), the combination of case study and GT approaches has three major strengths: it produces a novel theory, the emergent theory is testable, and the resultant theory is empirically valid (Mustonen-Ollila and Heikkonen, 2009). GT is used in interpretive studies, and it can be extended to inductive theory creation (Mustonen-Ollila and Heikkonen, 2009) – which is in line with this study.
The data should be categorised under several identifiable themes. These themes can also form the main categories or concepts in the data. This is a selective way of finding the concepts and categories in the data and is based on the researcher’s own intuition or knowledge. The concepts must be categorised according to relevant terminology and theories that form the most referenced work in categorising concepts in the research area. After the categories have been discovered, the number of categories must be decided on. The problem with the categories is whether enough proof can be found in the data to make them and the concepts valid and reliable, and whether the concepts and categories discovered are the correct ones. Some other concepts and categories may emerge from the data later. If the concepts and categories are not correct, the researcher must return to the data and discover new concepts. After the abstract concepts are found, they can be coded according to the instructions of Glaser and Strauss (1967), using selective coding to search the data categories. The abstract concepts can also be found using the content analysis approach (Krippendorff, 1985), which is a text analysis method. The approach requires the researcher to construct a category system, code the data, and calculate the frequencies or percentages that are used to test the hypotheses on the relationships among the variables of interest. It is assumed that the meaning of a text is objective, in the sense that a text corresponds to an objective reality.
The text is interpreted and understood without extraneous contextual knowledge. In case studies such as this study, the concepts are sharpened by building evidence that describes them. The data and concepts are constantly compared so that accumulating the evidence converges on simple and well-defined concepts, i.e. categories or constructs. The constructs are either ancillary or focal. In theory building, special focus is placed on dependent variables, that is, society and its IE. These concepts were the focal concepts (constructs) in the theory. The ancillary concepts (constructs) in the theory were the independent variables, which were associated with the changes in the value of the dependent variables. The conceptual framework tried to explain the changes in the values of these concepts. In this theory, the ancillary constructs were the defence strategies. The emergent relationships between the constructs were verified to fit the empirical evidence and GT was applied in their analysis. The data that confirmed the emergent relationships enhanced the confidence in the validity of the relationships.
In this study, the constant comparison between data and concepts in past studies, in order to accumulate evidence converged on simple, well-defined thematic categories, led to a higher level of abstraction of statements about the relationships between the thematic categories. This theorising was in line with Pawluch and Neiterman’s (2010) suggestions of creating a GT using Glaser and Strauss’s (1967) approach. The higher level of abstraction of statements is presented in the conclusions and discussion section. Glaser and Strauss’ (1967) study is the original study of the GT method (See also Pawluch and Neiterman, 2010). Intuition and knowledge is also used in determining the categories, and a chain of evidence is created: the thematic categories are derived from the empirical data and then validated using past studies. In this study, Pawluch and Neiterman’s (2010) GT analysis instructions, together with those of Glaser and Strauss (1967), support the finding of categories from data and based on the researchers’ own intuition and knowledge.
Strauss and Corbin’s (1990) GT method, on the other hand, uses three phases of coding as well as a tool (for example Atlas.ti) to define categories, and finally a core category. According to Strauss and Corbin (1990), GT has three levels of coding: open, axial and selective coding. Open coding reveals similarities and differences in the data so as to unveil the concepts, classes and relationships between the concepts in the data. Similar concepts will be put into the taxonomy of categories. There is a need to set the dependencies and relationships between concepts and classes: thus, in axial coding, categories are analysed. Through this, the development of the relationships between concepts will reveal new concepts and relationships. Selective coding integrates and refines the fully developed categories into theories. The main theme of the research emerges from the data during this phase, but after the main theory is established, the researcher still refines the categories by discarding the unwanted ones and expanding on those that remain poorly developed. In this study, however, the GT method of Strauss and Corbin (1990) was not applied but the differences between Glaser and Strauss (1967) and Strauss and Corbin (1990) needed to be addressed in order to avoid any disinformation.
A qualitative case study (Yin, 2003, Creswell, 2007) using the GT approach (Eisenhardt, 1989, Glaser and Strauss, 1967) was chosen to help answer the two research questions. The sample was limited to one society’s IE, because the goal of the study was to gain a deep understanding of the selected IE and to identify components of defence strategies at this specific site. Due to resource limitations, the sample was limited to 10 interviewed experts who represented eight different organisations in Finland. When the qualitative data reached saturation point, data collection ended. Nine audio-recorded unstructured and semi-structured interviews were conducted, which investigated the experiences of components of defence strategies. These interviews (Table 2) included eight individual interviews and one two-person group interview, which took place between January and May 2018. The interviewees were or had been involved in several components of defence strategy in their own fields of expertise during their working careers, which extended over a period of six to over 30 years in different positions and organisations in Finland and abroad. Archival material was also studied, representing a secondary source of data, which included public news and past scientific studies on components of defence strategies in Finland or abroad in general. Triangulation (Yin, 2003) was used to combine different data sources simultaneously to improve the reliability and validity of the data.
Table 2
Interviewee details
Each interview transcript was analysed and the major emergent themes and concepts were identified in order to form thematic categories (Myers and Avison, 2002). The interviewees received the questions before the interviews in order to familiarise themselves with them beforehand (Creswell, 2007), and were able to check their content in order to reduce mistakes. The questions were improved after each interview to better suit the next interview. In this in-depth case study, the interviewees recommended new interviewees based on their extensive experience in the area.
Data collection and categorization
The audio recorded interviews included frequent elaboration and clarification of meanings and terms, and the recordings were transcribed, yielding over 240 pages of transcriptions. After the transcription of the interviews, a qualitative research method based on GT (Glaser and Strauss, 1967) and content analysis (Krippendorff, 1985) was applied in order to categorise data under thematic categories according to relevant terminology and theories in the studied research area. In this study, the components of defence strategies were denoted as thematic categories (Glaser and Strauss, 1967). After creating the chain of evidence in data categorization, a total of 146 different empirical observations under 16 thematic categories (see Table 3) were found using Glaser and Strauss’s (1967) approach.
Table 3
Thematic category, definition based on empirical evidence, and total number of observations
Table 4 below shows an example of an observation concerning the ‘Cyber Defence’ thematic category. In Table 3, the first column contains a specific thematic category discovered in the empirical data; the second column contains its definition based on the empirical data; the third column contains its evidence based on the literature; the fourth column contains the literature references, and finally the fifth column contains the transcript number of the empirical evidence.
Table 4
Example of observation regarding ‘Cyber Defence’ thematic category
| Thematic category discovered in empiri- cal data | Definition of thematic cat- egory based on empirical data | Evidence from literature | Literature references | Tran- script number |
|---|---|---|---|---|
| Cyber Defence | Protection against foreign countries’ mili- tary and civil intelligence. | Cyber defence and cyber security are important parts of total defence. Cyber defence includes the combined capabilities of intelligence, influence and protection. It also includes both offensive and defensive measures, as well as devices and systems that are not con- nected to the network. | Lehto, 2016,Lehto et al., 2017 | TC7 |
Data analysis
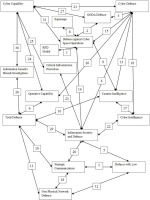
Fragmentation and reassembling was used to classify the data into thematic categories and thus capture the components of defence strategies in society’s IE (Glaser and Strauss, 1967). After the thematic categories were found, their properties and propositions (hypotheses) as to how they were related were determined. The conceptual framework (see Figure 1) shows the thematic categories as boxes, and the two-sided solid arrows with numbered small boxes describe the relationships between them. These relationships, based on empirical data, are presented in detail in Table 5. The constant comparison between the data and the thematic categories in past studies, in order to accumulate evidence convergence on simple and well-defined thematic categories, has led to a higher level of abstraction of statements about the relationships between the thematic categories. This theorising is in line with suggestions for creating a GT using Glaser and Strauss’s (1967) approach. The higher level of the statements’ abstraction is included in the discussion and conclusions section.
Table 5
Properties of thematic categories and propositions (hypotheses) as to how they are related on the basis of the data
Conclusion
Based on eight individual and one two-person in-depth group interviews, this qualitative, empirical case study based on the GT approach (Glaser and Strauss, 1967) tackled the thematic categories denoted as components of defence strategies in a society’s IE using the inductive research approach. The interview questions were improved many times, and sometimes due to the schedule of the interviewee, the questions were shortened. The largest interview consisted of 70 questions, and the ‘shortest’ of 30 questions. As already mentioned, the interviewees recommended new interviewees based on their extensive experience in this area.
The thematic categories were defined by building evidence from empirical data and describing it, which according to Glaser and Strauss (1967) are the building blocks of GT. The data and categories were constantly compared so that the accumulating evidence converged into 16 simple, well-defined thematic categories. After the thematic categories were found, their properties and propositions (hypotheses) as to how they were related were defined. Finally, a conceptual framework of the thematic categories and their relationships was developed. The comparison with past studies led to 9 higher-level abstractions of statements about the relationships between the thematic categories. This theorising was in line with suggestions for creating a GT using Glaser and Strauss’s (1967) approach.
Theory building in this study gave special status to the focal categories, that is, the society and its IE. In this theory, the ancillary category (construct) was the component of defence strategy. Boundary conditions were addressed in this theory creation, because the phenomenon was so atypical that it only held in this specific society’s IE. The results validated the conceptual framework, which became the discovered theory for the phenomenon. The data that confirmed the emergent relationships improved the confidence in the validity of the relationships. The past studies with similar findings were important because they tied together the underlying similarities in phenomena not associated with each other, achieving stronger internal validity.
This study is in line with the studies of Lehto (2016) and the Ministry of Defence (2006, p. 23) by finding that total defence protects a society’s citizens and vital functions from threats or actual attacks. This study is also in line with Lehto (2016) that an important part of total defence is military cyber defence, which is the combined capability of intelligence, influence and protection (Lehto et al., 2017). The results support the claims of Lehto (2015, p. 18) and Ottis (2013) that cyber defence needs network surveillance actions to protect the computer networks and information systems connected to the networks from cyber attacks and cyber operations. Furthermore, this study is line with Hausken (2019, p. 364) and Wei et al. (2015) that several networks in a society must be protected by cyber defence actions.
It also agrees with Yaghlane’s and Azaiez’s (2016), Wei et al.’s (2015), Lehto’s (2015) and Sigholm’s (2013, p. 51) studies observing that defence against military cyber space operations offers strategic benefits in cyberspace, and also Lehto et al.’s (2017, p. 33) claim that situation awareness and decision-making are better when cyber capability is at a high level.
The findings also support the claims of Lehto (2014, p. 54) and the Ministry of De-fence (2006) that defence systems need operative capability to get the wanted effectiveness to fight against threats.
The findings also support Mäntylä (2014), the Secretariat of the Security Committee (2018, p. 14), Dunn (2005), Geers (2011, p. 135), Hausken (2019, p. 364) and Quijano et. al. (2016): that society needs to protect its critical infrastructure because of its vital activities, and this protection also includes protection of the society’s services. The findings also support the claims of NATO StratCom COE (2016) that decision-making is affected by the distortion of the quality of information, not permitting access to information or decision-makers’ awareness of the information that they receive.
The findings are also in line with the Secretariat of the Security Committee’s (2018, pp. 16–17) view that information must be protected against breaches through investigations, and that we must learn from breaches in order to minimise damage.
The findings also agree with Von Clausewitz’s (1832) claims that espionage is needed for the state’s own purposes, to protect it and its society from foreign countries’ operations and plans.
The outcomes are also supported with the view of the Secretariat of the Security Committee (2018, p. 23), Clark (2013), Wihersaari (2015, p. 6) and Geers (2011, p. 100): cyber intelligence is needed to protect one’s own information systems and data communications, as well as the internet and other networks against hostile actors both inside and outside the state. The findings also agree with the Secretariat of the Security Committee (2018, p. 26), Mäntylä (2014, p. 14) and Geers (2011) who claim that defence against cyber spying – which is a part of cyber intelligence- is needed because networks, their devices and software targeted at states, citizens or any organisation or company using targeted malware attacks, must be protected against adversaries’ cyber spying.
The findings agree with Joint Publication 1–02 (2010, p. 53) which claims that in counter intelligence, information is gathered and defence activities are conducted against hostile intelligence actors for their activities against us.
The study results are in line with those of NATO StratCom COE (2016) and Cline (1993, p. 147) in that the Recognition Primed Decision (RPD) Model of Rapid Decision Making protects decision-makers’ ability to make the right decisions in a hostile environment.
This study is in line with those of the Secretariat of the Security Committee (2018, p. 15), Hausken (2019, p. 364), Nimmo (2015), Pomerantsev (2015), Mäntylä (2014) and Raggad (2010) in its finding that information security and defence protects information confidentiality, accessibility and reliability from unauthorised actions. The results agree with the Secretariat of the Security Committee (2018, p. 14), Mäntylä (2014) and Dunn (2005, p. 261) in their claim that information, data and software inside computer and information systems must be protected because they operate inside physical infrastructures. In addition, they also support Dunn’s (2005, p. 261) claims that information protection is at the level of national security because information infrastructure is dependent on ICT.
The findings also agree with Jackson (2015, p. 6) that Defence with Law prevents the incorrect usage of legitimate systems.
The findings are also in line with the studies of the Ministry of Defence (2016), Lehto (2015), Sillanpää et al. (2015), the Joint Chiefs of Staff (2013) and Schechtman (1996) in that OODA is needed to defend IE, by defending it against IO, cyber operations or network exploitation.
The findings support those of Conley et al. (2016) that non-physical network defence is needed against networks that are guided, owned and funded by a foreign state and opaque foreign state networks.
The findings agree with Luoma-aho (2015), Jantunen (2015), NATO StratCom COE (2015), Hollis (2011) and the U.S. Department of Defence (2008) that StratCom is needed for protection against hostile IO and psychological operations and to carry out one’s own IO and public relations influence targeted at domestic and foreign media and audiences.
In this study, these components of defence strategies were inter-related, 9 higher levels of abstraction of statements, based on the conceptual framework, the propositions for the components of defence strategies, and the relationships between the components of defence strategies were found. 1) With the right cyber capability, OODA defence and cyber defence actions, it is possible to defend and protect society’s IE, and to improve cyber capability. 2) Information security and defence, critical infrastructure defence, and cyber defence must be up to date because these are the most important to defend and protect. 3) The actors working with the information must be aware of their own actions related to the information. 4) Cyber defence needs counter-intelligence, cyber intelligence, and OODA defence to make decisions very quickly in order to defend society against cyber operations and cyber attacks. 5) Cyber defence improves cyber capability and is vital for defence against cyber operations. It is needed in operative capability and cyber defence is related to information security and defence. The means to improve cyber defence are counter-intelligence, cyber intelligence and OODA defence. 6) Information security and defence is closely related to cyber defence, and it can be protected and defended by cyber intelligence, through law and strategic communications. Information inside the critical infrastructure needs protection from information security and defence. Information security and defence is also needed in total defence and defence against cyber operations as regards the information needed in these two latter categories. 7) Defence against cyber operations needs espionage, OODA defence, counter-intelligence, and RPD. Information security and defence improves cyber capability and protects information inside one’s own cyber operations. 8) Information security breach investigation helps cyber capability because this capability consists of information systems’ capability and operative capability. Operative capability needs information protection and if information is under attack, military attack goals may not be achieved if one’s own information is known by the adversary when it is leaked. Information security breach investigation also helps total defence because it helps find the attacker of the information and helps find what information the hostile actor now has. Information security and de-fence needs information security breach investigation in order to protect the information and to know what new protection solutions are needed to defend one’s own information. 9) Non-physical network defence needs strategic communications, and defence with law. Non-physical network defence is part of total defence. Protecting it improves total defence from foreign states’ goals to destroy society’s IE.
Eleven conclusions emerged from this study. 1) The data and findings showed 16 different interconnected components of defence strategies. 2) The hostile actors’ political, military, societal, power and personal goals for carrying out cyber operations and cyber attacks is to weaken society’s IE. 3) Cyber operations and cyber attacks against networks, information and infrastructures are coordinated operations, carried out over a long time period. 4) The actors defending society’s IE must rapidly change their own components of defence strategies, if necessary, and use the newest tools, methods and components of defence strategies in networks, infrastructures and social media networks, which connect a great deal of people. 5) The adversary uses its own espionage and intelligence to investigate important information, information systems and networks before it makes a cyber attack or cyber operation on them. Espionage and intelligence have taken a long time and, by taking these actions, the adversary can define its attack targets. 6) The network attack or cyber attack can also start very slowly with small targets, and defenders might not even see them at first, or it may not be possible to understand what is going on. The defender must distribute its components of defence strategies to many places at the same time, and this ties up the defender’s resources. But, if a new, stronger attack starts to take place at the same, then the defender may lack defence resources. 7) It is also possible that not all targets under attack are even noticed, because many attacks are taking place at the same time. The defender can protect and defend its sources by preventing the adversary from going further and deeper into the information systems and networks, or not even revealing that the defender knows the adversary is there harming the systems and networks. 8) If an attack has taken place, it is not always known whether the attacker has left “something inside the systems and networks” and can carry out a new attack later by using these. The defender can use its own intelligence to find out what the attacker is going to do in the future, but the attacker can use previously unused intrusion methods and get inside. 9) The defender can protect its networks by hiding them and their traffic, or by using firewalls or their own cyber intelligence and network surveillance, which alert when they are under attack. The attacker can even use secured systems for their own purposes by buying out some individuals in a company who are actually working for them, not their employer. These internal spies are a severe threat because they can work freely inside the systems, without anybody noticing what they are really doing. These spies can harm the systems even more than a real attack. 10) One way to defend systems and networks is to build them up in such a way that an attacker can only enter restricted areas and cannot harm any information that is important and vital for society. 11) Citizens must be informed about attacks on a certain level, honestly, so that they understand that they must protect their own information, information systems and networks, and keep their own privacy in good condition so that they and their computers cannot be used as tools in attacks. How and when to inform citizens should be considered carefully. It must be also remembered that attackers will be informed at the same time because they follow the open news about attacks and also realise that their attack is not taking place in secret, but is known publicly.
The practical and managerial contribution helps defending actors outline what components of defence strategies exist in the society’s IE and how these components of defence strategies are related to each other. An important practical contribution was the large number of components of defence strategy observations in practice. The managerial contribution lies in making every decision-maker in the society’s IE aware of these components of decision strategies and to understand how they affect society’s IE.
The methodological contribution is how diverse qualitative research methods, such as GT (Glaser and Strauss, 1967), content analysis (Krippendorff, 1985), and rigorously applied methods can be used together to conduct a high-quality literature study (Wolf-swinkel, Furtmueller and Wilderom, 2013).
This study has several limitations. First, as components of defence strategy is very large as a research area and contains many issues, it was impossible to cover all of them. Second, trying to determine suitable thematic category definitions for 146 observations was a difficult task, and took longer than estimated. Third, for some of the observations it was challenging to determine the thematic category where it ultimately belongs to. Fourth, the use of only one society’s IE affected the findings, and thus generalisation of the results may be that straightforward, although definitely not impossible. Fifth, a limited number of interviews were conducted: only 10 people were interviewed. Sixth, the problem with the thematic categories was whether there was enough proof found in the data to derive these components of defence strategies as valid and reliable, and whether the thematic categories discovered in the data were the correct ones.
In the future, a quantitative analysis of components of defence strategies will be conducted. Glaser and Strauss (1967) and Eisenhardt (1989) claim that both qualitative and quantitative data can be used for creating a new theory. These two types of data can indeed supplement each other and their comparison can result in new theory.